How to Refine your Search Results Using Grep Exclude
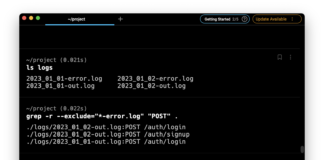
What is Grep Exclude?
Grep exclude is a powerful feature of the grep command...
Monitoring Server: Install Zabbix on an Ubuntu 16.04 Server
Monitoring Server - What is Zabbix
Zabbix is an enterprise-class open source distributed monitoring server solution. The software monitors different parameters of a network and...
How to Install Latest GIT on RHEL 6/CentOS 6
So you want to setup a GIT Repository for your developers on RHEL 6/CentOS 6, but notice Red Hat Enterprise Linux 6 contains 1.7.1...
Fixin AttributeError: module ‘pkgutil’ has no attribute ‘ImpImporter’
Understanding the Error
The error "AttributeError: module 'pkgutil' has no attribute 'ImpImporter'" typically occurs when running Python code that uses the pkgutil module, specifically when...
How to Disable SSH Root Login in GNU/Linux
As we all know, root SSH login is enabled by default in GNU/Linux. We can easily access our remote servers and manage them if...
Determine Your Specifications from Command-Line
We recently published article about how to determine your computer's architecture via GUI. Today am going to show how to do the same thing...
TaskBoard: Kanban-based Software on CentOS 7
Introduction
TaskBoard is a free and open source software, inspired by the Kanban board, for keeping track of things that need to be done.
Kanban is...
VI Save and Exit: Essential Commands in Unix’s Text Editor
What is VI?
VI, short for "Visual Interface," is a powerful text editor that...
Continuous Integration: Concourse CI on Ubuntu 16.04
Concourse Continuous Integration System
Concourse CI is a simple and scalable continuous integration system with an end goal of providing a system with as few...
Useful Commands for Linux Users – Episode 5
The Command-line is more powerful because you can do lots with them. Yyou can tell your computer exactly what you want and get the...
Install FreeBSD 10 Step by Step
This RC build of the 10.0-RELEASE is now available on the FTP servers for the amd64, i386, ia64, powerpc, powerpc64 and sparc64 architectures.
Changes between...
Install LAMP (Apache, MySQL And PHP) On Debian 7 ‘Wheezy’
LAMP is a combination of operating system and open-source software stack. The acronym LAMP is derived from first letters of Linux, Apache HTTP Server,...
Using the CP Command to Copy A Directory on Linux
Copying directories is a vital task in Linux systems administration and everyday use. Whether you're backing up...
FreeBSD 10.1 x64 WiFi Captive Portal
Our goal is to build a FreeBSD server Captive Portal as it is in hotels and airports. Guest joins to wifi without entering a...
SED Replace: How to Manipulate Text in Unix
So, what is SED Replace?
SED stands for Stream Editor. This is a powerful...
Use Terminal as a Web Browser
Web browsers are software used to access and view the internet and webpages. We all know about some of the popular web browsers such...
Installing Invoice Ninja on CentOS 7 w/ NGINX & MariaDB –...
Introduction
Invoice Ninja is a free and open source invoicing system. The site also provides invoicing through Software as a Service (SaaS). But, of course, it's...
Linux vs Unix – How is UNIX different from Linux
Linux and Unix are two terminologies that are interchangeably used to refer to the same Operating system. This is largely due...