How to Chroot SSH Users on Centos 7
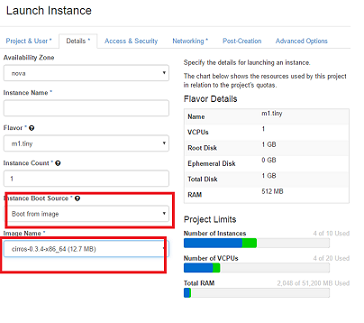
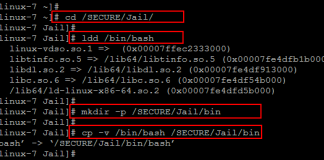
The term chroot refers to a process of creating a virtualized environment in a Unix operating system, separating it from the main operating system...
Linux vs Windows: Here are 9 Most Essential Differences
Linux and Windows are the two most popular operating systems for personal computers. Both of the systems have different purposes and functionality. But each...
Setting Up and Running A Container Registry On Linux
Docker container images are delivered and stored by an application called Docker Registry. Registries consolidate container images and speed up developer build times. Virtualization...
Tighten the Security of Linux Servers
What is Linux?
The simple and straightforward meaning of Linux is the operating system used to build a connection between the software resources and the...
Risks to Consider When Using Linux
Linux is a free and open-source operating system that's popular among developers, businesses, and individuals. The flexibility and customizability of Linux make it an...
Optimizing Web Performance with Linux: Tools and Techniques
Providing fast, well-performing websites is absolutely essential these days. A slow website means visitors will drop off sooner and leave, missing opportunities and leaving...
Unveiling the Life Stories of Linux Innovators
Linux, the open-source operating system that powers millions of devices worldwide, is a testament to the collaborative efforts of countless innovators. While the Linux...
A Closer Look at Remote Peering: Technologies and Techniques
In the realm of digital communication, the significance of efficient internet traffic exchange has escalated with the...
How to Install VirtualBox on Ubuntu and Create a Virtual...
Virtualbox is a very simple & powerful virtualization tool that is used to create & manage Virtual Machines . Most of my friends &...
Best Linux Distros for Small Businesses
There’s a wide variety of Linux distros out there —built for all kinds of purposes and user types. The top ones are made to...
How Businesses Can Benefit from Using Linux
Many businesses spend a lot of time weighing up the benefits of cloud automation and orchestration, without spending too much time considering operating systems....
The Advantages Of Linux Over Other Operating Systems In Business Processes
Linux has become a go-to option for many businesses in recent years. There are a number of reasons why this is the case, but...
Best VPNs for Linux with and without GUI
The Linux operating system takes up a tiny portion of the market because it appears daunting to the average person. It’s commonly known as...
How to Recover Deleted Files in Linux I Guide
Files management is an important skill for everyone who utilizes storage devices for whatever reason. File recovery tools for instance are crucial utilities you...
Enhancing User Experience: How Linux OS and Localization Drive Global Success
In the ever-evolving landscape of technology, user experience (UX) has emerged as a critical factor in determining...
Harnessing the Power of Free VPNs for Enhanced Cybersecurity on Linux
Safeguarding our digital footprint is now crucial in the ever-expanding digital ecosystem where risks to online security...
How To Compile And Install OTClient On Ubuntu 16.04
This article is about downloading , compiling and installing the OTClient. We will explain the step by step procedure for downloading, compiling and installing...
How to prevent a Supply Chain Attack in a Linux Environment
What is a supply chain attack?
This is a type of cyberattack that seeks to damage an organization by attacking weaker elements in the supply...