5 Best Ways To Secure Your Linux System Distribution
There are many ways to secure your Linux system distribution. Today, cyber attacks and computer hacking can be prevented by bolstering security systems. By...
5 Data Security Issues on Linux
Every tech enthusiast knows that Linux comes with the freedom that hardly any other OS can offer. We don’t even have to get into...
6 reasons why Linux is an ideal solution for programming
Today we will talk with you about Linux, an operating system that is gaining popularity simultaneously with the development of open-source software, and its...
Linux-Based Safety Management Software: A Comprehensive Guide
Safety management software is a crucial tool for businesses to effectively manage workplace safety, reduce risks, and maintain compliance with industry regulations. In today's...
Should You Use Linux For Backend Development in 2023?
With Backend Development, a developer finds thousands of interesting options to develop, deploy and manage these server-side applications. As technology is growing over time,...
How To Install Kali Linux in VirtualBox (Step by Step)
The Debian-based Kali Linux is one of the best-known Linux distros among cybersecurity professionals. Previously known as...
How to Secure File Uploads on Linux Servers
File uploads are a common feature in many web applications, but they also introduce significant security risks...
Tar Command in Linux: A Step-by-step Guide to Mastery
At Unixmen, we have been explaining each and every important Linux command in detail that would help...
Understanding Symlink: Beginner’s Guide to Symbolic Links
What is a Symlink?
A symlink, short for symbolic link, is a special type of file that serves as a reference or pointer to another...
AI Voice Generators: How Linux based Platforms are Crafting Authentic Narratives...
The digital age has brought about a myriad of technological advancements. Each progress path has helped reshape various industries. And there is no better...
Simple Strategies for Achieving End-to-End Security in Web3 Audits
Prioritize a thorough code review. Engaging experienced developers familiar with decentralized frameworks can unearth vulnerabilities that might be overlooked. Employ automated tools for initial...
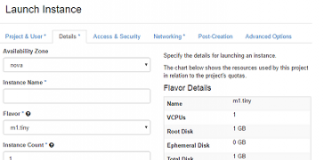
How To Create Instances (Virtual Machines) With External Network Connectivity In...
Hello Friends, today we will discuss how to create virtual machines (known as "instances" in openstack terminology) using Horizon Dashboard. We tested these steps...
How To Install And Use Google Drive Desktop Application OverGrive On...
Hello Readers, today we will be learning about OverGrive and its installation process on Ubuntu Linux. OverGrive is the desktop application for Google Drive; which...
Why It Is Better To Program On Linux
You have probably heard a lot of times that it is better to program on Linux, and programmers use it more often than Windows....
Bash While Loop Examples: For Loops, Until Loops, And More
Bash programming comprises three kinds of loops: the for loop, the while loop, and the until loop. The idea of all the loops is...
How To Use ldd Command in Linux with Examples
If you're using a Linux machine, you will be dealing with executable files constantly – be it on the GUI or on your terminal....
A Guide To Implementing Segregation of Duties (SoD) in Linux Environments
In today's ever-evolving cyber threats, organizations must implement robust security measures that safeguard their valuable data and resources. One such essential measure is the...
Essential Cybersecurity Tools for Linux in 2023
In today's digital happenings, taking serious cybersecurity measures is crucial to protect sensitive information from cybercriminals, especially for corporate organizations with high levels of...