How to Leverage the Power of Predictive Analytics on Linux
Among the many impressive tools and applications of big data, predictive analytics stands apart as one of the most effective. By utilizing statistical models...
4 Reasons Why You Should Choose RHEL Over CentOS
Linux is the preferred operating system for production servers and critical systems. Linux has over 300 popular flavors / distributions that are being used all...
How to Develop a Reliable Startup Utilizing the Linux OS
It comes as no surprise that the Windows OS and the Microsoft environment are some of the most common infrastructures to be found within...
Debian-Based Distro OpenMediaVault 2.1 [Stone burner] is out now. Prominent Features...
OpenMediaVault is a free Network Attached Storage operating system, it is an architecture independent Linux distro; which means it can be installed on any type...
A List of NTFS for Mac Software: What It Is and...
New Technology File System (abbreviated to NTFS) is a widely used file system on Windows. By default, you have direct read-write access to NTFS-formatted...
System Rescue Live CD OS – SystemRescueCd 4.6.0 is out now
SystemRescueCd is a Live CD/DVD operating system that is used for system maintenance tasks. It is a blessing for system administrators as they can...
Testing Tails 1.5 RC1 Incognito Live CD
Tails is a Debian based live operating system which can be booted from USB, CD/DVD or SD card and lets you browse internet anonymously....
What Are the Best Programming Languages for Linux Devs?
If you are on the path to becoming a Linux developer, surely you will understand that computer science and programming are a core part...
Point Linux 3.0 Is Out Now. Distro Review
If you love Debian, but miss GNOME 2; you should definitely try Point Linux. It comes with MATE desktop environment which is fork of...
Linux Training Model: What A Linux Course Should Look Like
Whether you’re an independent developer trying to design a course and sell it or need to make material to introduce employees to using Linux,...
Switching To Linux Mint: The Benefits and Drawbacks
Deciding to spend hundreds of dollars on new hardware – be it a laptop or a desktop component – is always a tough call....
Linux Antivirus: Security in Open-Source OS
Introduction
While Linux systems are generally considered more secure than their Windows counterparts, they...
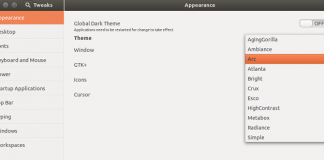
How to install Arc GTK Theme on Ubuntu 15.04
Arc is flat, beautiful, gorgeous GTK theme for Linux distributions. GIMP Toolkit (abbreviated as GTK), is cross platform toolkit for creating graphical user interfaces....
Transcription Services on Linux: A Guide to Enhancing Productivity and Efficiency
Transcription services on Linux are becoming increasingly popular, offering users a better way to increase their productivity and efficiency. By leveraging the open-source nature...
The Best Private Browsers for Linux
Does the phrase private browser ring a bell? Considering the questionable digital privacy conditions, such programs are becoming increasingly popular.
A private browser is a...
Linux Server Provisioning Using StackI
Server provisioning is a set of actions to prepare a server, taking it from bare metal to a functioning system complete with an operating...
New Robolinux “Mate Raptor” – Powerful, Feature-Rich, Elegant
Introduction
Robolinux is a popular choice for users migrating from Microsoft Windows to Linux operating system. It is a Debian based operating system and has...
Best VPNs for Linux with and without GUI
The Linux operating system takes up a tiny portion of the market because it appears daunting to the average person. It’s commonly known as...






![Debian-Based Distro OpenMediaVault 2.1 [Stone burner] is out now. Prominent Features and Installation Guide Open Media](https://www.unixmen.com/wp-content/uploads/2015/07/1-1-324x160.png)