How to Create Binds in Linux for CS2
Binds have been a fundamental part of Counter Strike since its early versions, and their usefulness remains undeniable even with the release...
SSH Max Limits and Optimization
SSH (Secure Shell) is a powerful tool for remote administration and secure data transfer. However, it's crucial to understand and configure its limits effectively...
Roofing SEO Agency + Linux: Elevate Your Roofing Business with Open‑Source...
In today’s digital landscape, online visibility is paramount for any business’s success—and roofing companies are no exception. In a crowded market, differentiating yourself is...
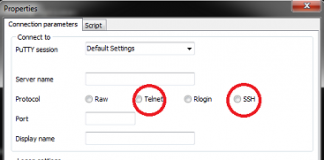
Difference between Telnet and SSH
Being a system administrator, it is one of our key responsibilities to manage & monitor the production & enterprise servers, upgrading their kernel, installing...
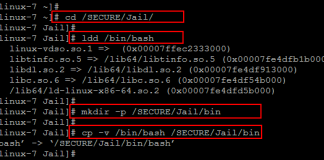
How to Chroot SSH Users on Centos 7
The term chroot refers to a process of creating a virtualized environment in a Unix operating system, separating it from the main operating system...
How Open Source Operating Systems Can Be Ideal For Your Business
In a world where Windows has become synonymous with PCs in the minds of the public, is there room for Open Source Operating Systems...
6 Factors that Make Linux Important for your Small Business
A huge number of modern companies know about Linux firsthand. Many of them have been using various distributions in one form or another for...
Fsck: How to Check and Repair a Filesystem
Every operating system needs a mechanism to store and recover data. This mechanism is called the filesystem.
But the odds of a filesystem failing increase...
How To Install and Use the Linux Bat Command
The bat command works just like the cat command does on Linux. The difference is that the bat command is more modern, boasting a...
3 Reasons Why Linux is the Best Choice to Achieve Optimal...
With technological advancements, hackers are becoming increasingly adept at identifying vulnerabilities and gaps in security systems. This makes unauthorized access to secure data and...
Linux Leaps Ahead: Dynamic Future of Linux in 2024
As we journey through 2024, the world of Linux is witnessing a fascinating evolution, shaping the technology...
How to Fix the SSH Permission Denied (publickey) Error
Introduction
SSH, or Secure Shell, is an essential protocol that is widely-used in the...
Linux: Set Environment Variables—An explanatory guide
In Linux, set environment variables to define system behaviour. Ensure that all applications work as they are...
What is ‘sh’
Introduction to 'sh'
In the world of Unix and Unix-like operating systems, 'sh' stands for "shell," specifically referring to the Bourne Shell. But what is...
LUKS: Detailed Guide to Linux Unified Key Setup
LUKS (Linux Unified Key Setup) is the default encryption method for Linux distributions. It provides robust full-disk encryption. If you put security at the...
How To Compile And Install OTClient On Ubuntu 16.04
This article is about downloading , compiling and installing the OTClient. We will explain the step by step procedure for downloading, compiling and installing...
How to install Kali Linux on your PC
Based on Debian Kali Linux is a free and opensource operating system that is popularly used for penetration testing, ethical hacking, and...
The Five Reasons Why Techies Are Obsessed With Linux
We all know people who are obsessed with tech. For the vast majority, it’s people obsessed with the more traditional forms of the media...