XWiki Installation in Linux
XWiki
Xwiki is an open-source enterprise-ready wiki written in Java, runs on a servlet container like Tomcat, Jboss etc. which uses the relational database to...
How To Install Ubuntu 21.04 With A Virtual Machine
Ubuntu 21.04, nicknamed "Hirsute Hippo" was released in April 2021. The Ubuntu family of operating systems is renowned for its stability and ease of...
How to Install Cinnamon 3.0 On Ubuntu 16.04 LTS
As you all already know that Ubuntu 16.04 LTS is out there so today we will come to know how we can install & work...
Top 10 Benefits of Linux for App Development
Linux appeared in 1991 and remained one of the top systems for developing practical solutions. It is one of the best-loved bases for app...
Switching To Linux Mint: The Benefits and Drawbacks
Deciding to spend hundreds of dollars on new hardware – be it a laptop or a desktop component – is always a tough call....
Create USB bootable disk using GNOME Disks
By default, Ubuntu ships with Ubuntu startup creator application to create bootable USB drive. For those who don’t know already, there is another builtin...
The Benefits of Choosing Linux Over Other Operating Systems
Linux is a powerful, open-source operating system that is becoming increasingly popular among computer users of all kinds. It is known for its stability,...
How to install Snap in Fedora24
Snappy Package Manager
Snappy package manager is a transnational package manager. Originally it was built for Ubuntu Operating system, But now it available for all...
How To Unrar a File: Unix and Linux
Applications, images, documents, and other files of all sorts are most commonly shared across the internet in the RAR format. It is a compressed...
Best Marketing & SEO Software For Linux
Being one of the safest and risk-free types of operating systems and trusted computer ecosystems on the web, Linux became a popular OS among...
Compare NetSuite and Red Hat Enterprise Linux
What is Netsuite?
NetSuite is a cloud-based enterprise resource planning (ERP) software that provides business management solutions for various industries such as retail, wholesale distribution,...
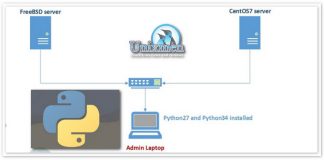
Python Auto deploy LAMP in centos7 and FreeBSD 10.x
In this Article we will show you how to deploy and full Lamp ( Apache /MariaDB server /Php) stack installation from your laptop or ...
Tighten the Security of Linux Servers
What is Linux?
The simple and straightforward meaning of Linux is the operating system used to build a connection between the software resources and the...
What Are Some Ideas to Improve a MacBook’s Performance?
If your MacBook is relatively old, you might have noticed that it is not performing as great as it did early. While Macs are...
Ways to Enhance the Security of Your Linux Server
Security has always been the cornerstone of any Linux software. Since Linux is open-source software, people can audit code to find and patch any...