Linux/Unix Programming: How AI Machine Learning Can Save You Time and...
Linux/Unix programming has entered a new era where ai machine learning technologies revolutionize development workflows, dramatically reducing time spent on repetitive tasks while enhancing...
Roofing SEO Agency + Linux: Elevate Your Roofing Business with Open‑Source...
In today’s digital landscape, online visibility is paramount for any business’s success—and roofing companies are no exception. In a crowded market, differentiating yourself is...
The Common Linux VPS Mistakes Beginners Make (And How to Avoid...
For developers, website owners, and tech-savvy entrepreneurs, a Linux virtual private server (VPS) offers flexibility, power, and control at an affordable cost. However, for...
Parcel Tracking and Linux: Using Open-Source Tools for Delivery Management
In today’s world, managing shipments and packages has become an important milestone for both personal and business use. For Linux enthusiasts and those who...
Simple Strategies for Achieving End-to-End Security in Web3 Audits
Prioritize a thorough code review. Engaging experienced developers familiar with decentralized frameworks can unearth vulnerabilities that might be overlooked. Employ automated tools for initial...
Healthcare Software Development: A Comprehensive Overview
In today’s rapidly evolving digital world, healthcare software development has emerged as one of the most pivotal aspects of the medical and health industry....
AI Software For Linux: Which Linux AI Tools Are Best in...
AI Software For Linux: Which Linux AI Tools Are Best in 2025?
Artificial Intelligence is no longer just a trend; it’s the backbone of every...
shopt in Bash: How to Improve Script Reliability
There are multiple very useful built-ins in Bash other than cd, ls, and echo. For shell scripting and terminal command execution, there is one...
Markdown: How to Add A New Line
When working with Markdown, understanding how to create new lines is essential for proper formatting and readability. This guide will explain everything you need...
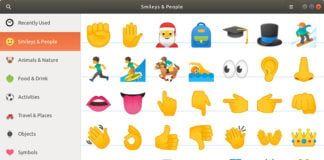
How to Type Emojis in Ubuntu Linux
Emojis have become an essential part of modern digital communication, adding emotion and context to our messages. While typing emojis is straightforward on mobile...
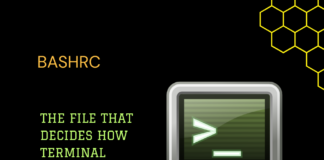
.bashrc: The Configuration File of Linux Terminal
Today at Unixmen, we are about to explain everything there is about the ".bashrc" file. This file serves as a script that initializes settings...
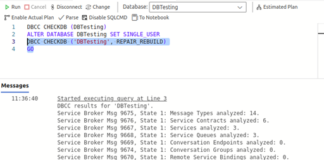
Linux SQL Server Database Recovery: Restoring Corrupt Databases
Microsoft MS SQL server supports Linux operating systems, including Red Hat Enterprise Linux, Ubuntu, and container images on Virtual machine platforms like Kubernetes, Docker...
Best Way to Document Harmful Content for Removal
Have you ever searched your name or your brand and found content that you didn’t expect to see?
Maybe a page that doesn’t represent you...
Linux Tips and Tricks: With Recent Updates
Working with Linux is easy if you know how to use commands, scripts, and directories to your advantage. Let us give you some Linux...
How Does Open-Source Code Influence the Development of Bots?
When people think of the word ‘bots’, they often think of it in negative terms. Bots, of course, are one of the biggest threats...
Markdown Italics: Instructions, Pitfalls, and Solutions
There are plenty of markup languages available. This page is written on HTML, a markup language. One of them is Markdown, a lightweight markup...
JSON Checker: Validate and Debug JSON Files
What is JSON Checker?
It is a tool (most of the cases), or a script (the backend) used to validate and verify JSON (JavaScript object...
Why Every Linux/Unix User Should Try Creative Fabrica’s Font Generator
Typography isn’t just for designers—it plays a vital role in programming, terminal applications, system interfaces, and documentation readability. Whether you’re customizing your Linux desktop,...