Setting Up and Managing Proxy Servers on Linux
Your Linux system might be performing well, but do you know a proxy server could boost its...
Popular Linux Software Contracts for Businesses
Linux has become a critical component of the IT infrastructure for many businesses, known for its stability,...
How To Setup A Proxy Server: A Beginner’s Guide For Linux...
So, you want to set up a proxy server on your Linux machine? That’s awesome!
How to Add User to Sudo Group on Ubuntu 24.04
When you fresh install Ubuntu 24.04 and create a user, that user is added to sudo group...
How to Change a Git Commit Message
What is a Git Commit Message
Once you get deep into programming and software...
VI Save and Exit: Essential Commands in Unix’s Text Editor
What is VI?
VI, short for "Visual Interface," is a powerful text editor that...
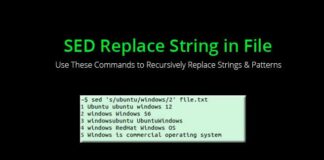
SED Replace: How to Manipulate Text in Unix
So, what is SED Replace?
SED stands for Stream Editor. This is a powerful...
LS Command: How to List Files in Unix Systems
What is the LS Command?
If you occasionally use Linux and Unix based operating...
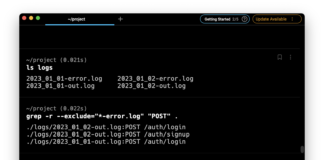
How to Refine your Search Results Using Grep Exclude
What is Grep Exclude?
Grep exclude is a powerful feature of the grep command...
Enable SSH Ubuntu: How to Securely Access your Remote Server
Learning how to enable SSH (Secure Shell) on Ubuntu is a crucial step...
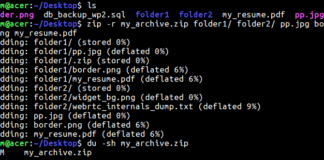
How to Compress Files Using the Linux Zip Command
The Linux zip command is an essential tool for file compression and archiving in Unix-based systems. Whether...
Navigating Cybersecurity Threats with Linux and Anonymity Tools
Despite the numerous benefits and advantages, we get from the Internet and Information Technologies (IT), the connectivity...
Leveraging Linux/Unix for Preventing Repeat Signups in E-commerce
E-commerce websites face a range of challenges, from managing inventory to ensuring secure transactions. One often-overlooked issue...
Elementor Website Design Templates: Jumpstart Your Creative Process
Do you want the Elementor website design templates? Which things should you notice in the website designer...
Crash Course on Organizing Your Workday on Linux
Crash Course on Organizing Your Workday on Linux
As a Linux distribution user,...
Unlock the Power Reverse Email Lookup With Linux: Improving Security and...
Email is a major communication mode in today’s digital era. Whether you use it for personal interactions,...
How Threat Intelligence Reduces Cybercrime
Companies that perform most of their operations online risk being attacked by cybercriminals trying to steal their...
The Role of Outsourcing in Web Development for Linux Software Solutions
Outsourcing web development plays a pivotal role in successfully executing Linux software solutions. How to outsource web...