Ubuntu14.04 OpenVPN FreeRADIUS Active Directory integration
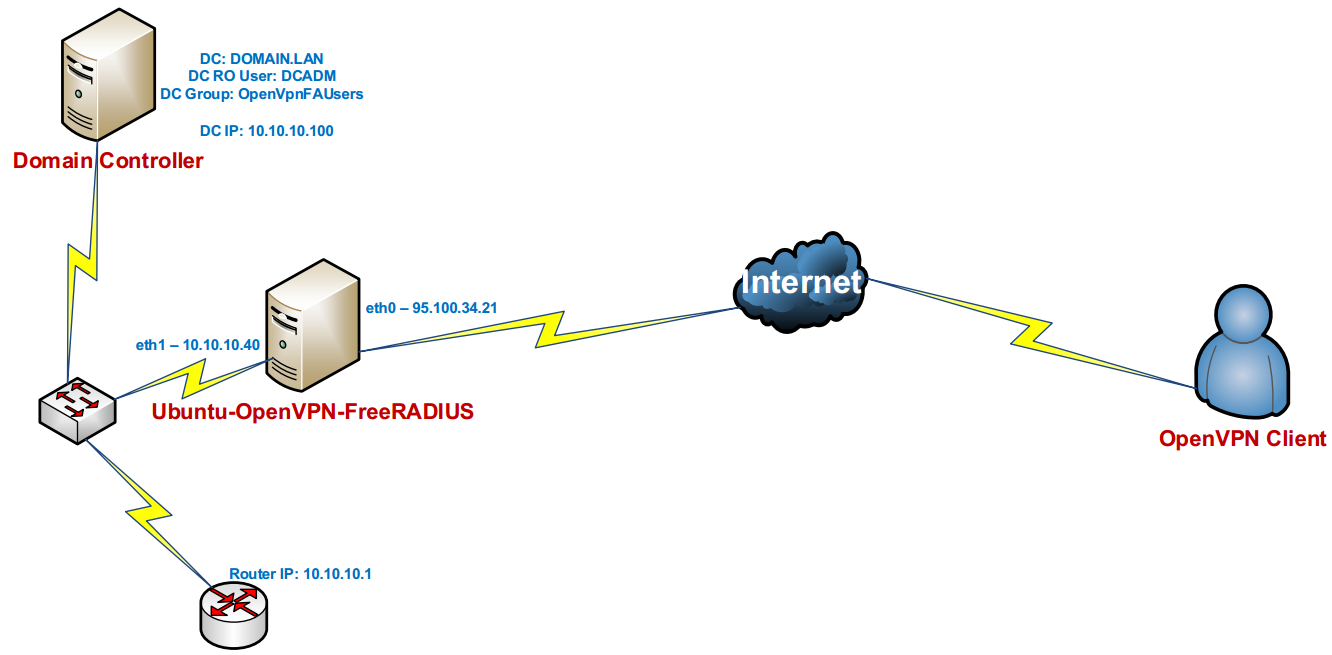
Our purpose is install and configure OpenVPN server on Ubuntu 14.04 and after integrate this with FreeRADIUS. After successful configuration OpenVPN with FreeRADIUS, we will integrate FreeRADIUS to Active Directory. Then, user from AD LDAP group must connect to OpenVPN server. The network infrastructure will be as follows:
Used Operation Systems:
Windows 2012 Server R2 – Domain Controller
Windows 8.1 x64 – Client desktop
Ubuntu 14.04 x64 – OpenVPN server
Active Directory credentials will be as follows:
Domain Controller: domain.lan
DC RO User: DCADM
DC VPN Group: OpenVPNFAUsers – Users in this group will be full access to corporate network(It means virtual subnet of our OpenVPN take all routes from corporate core Router)
Windows 8.1 client configuration file will be as follows(file name is domain-ad-auth.ovpn). The extension of file must be .ovpn:
client
auth-user-pass
auth-nocache
proto tcp
remote ovpndc.domain.az
port 1194
dev tun
nobind
key-direction 1
ns-cert-type server
# ca.crt file which is created in OpenVPN server
<ca>
—–BEGIN CERTIFICATE—–
MIIGxDCCBKygAwIBAgIJALsV/eQc/V5+MA0GCSqGSIb3DQEBBQUAMIGcMQswCQYD
VQQGEwJBWjENMAsGA1UECBMEQkFLVTEUMBIGA1UEBxMLWWVuaVlhc2FtYWwxFDAS
BgNVBAoTC0FUTEluZm9UZWNoMQswCQYDVQQLEwJJVDEXMBUGA1UEAxMOQVRMSW5m
b1RlY2ggQ0ExLDAqBgkqhkiG9w0BCQEWHWphbWFsLnNoYWh2ZXJkaXlldkBhdGx0
ZWNoLmF6MB4XDTE0MDYwODE3NDUzOFoXDTIzMDYwNjE3NDUzOFowgZwxCzAJBgNV
BAYTAkFaMQ0wCwYDVQQIEwRCQUtVMRQwEgYDVQQHEwtZZW5pWWFzYW1hbDEUMBIG
A1UEChMLQVRMSW5mb1RlY2gxCzAJBgNVBAsTAklUMRcwFQYDVQQDEw5BVExJbmZv
VGVjaCBDQTEsMCoGCSqGSIb3DQEJARYdamFtYWwuc2hhaHZlcmRpeWV2QGF0bHRl
Y2guYXowggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQC0kYn6jZf/R1eA
Xs1YH/g36sIQJcxJBmcbXh/atZTy7W8rlXsCw05+RU7OaXrFQUEbed0lnjYiKfri
CutMpT5c7iY6fgfMMoPaIqk8q17qydk8HvqQoac3kjo9wMD7XWlDYiLFk1FxQjEW
BIqI2z6vh9/9ka54s6WNRgzT+7+EZqSuwCfC6Dm/0qxp4AvEjapwjaURJ6yEuQYe
Odh5ydTsIcueNnBzkuFZRx5O5iNcaBQZ2fUVpQvueTCCsHkPt1BGU3TqWIYTUVZl
O4wPQoOyXC9YUvWaYWSLTDMNDvCvGFYfc5C3++nijtfWpO8LLDZgiwC7ScYj+Boo
SZ9dkEpIYdb03KBnn+LCO3STVukpwTr+vyKjPITceuElHXdWvXi7wgtopwQhQ+3j
sDCvB+Wg2Bt5zBPC43WTeLANOGZFQN1f1kyBNXlBm1tM0kl3k75skkj9TXHjrM44
+aVdxlPjkQ86e6/A04wCUOBNf4aO0Q8r6PWCfpkqatDn6hCh6ChAYYuqAR5W3eRs
p2D3lAWGEHlBlf/+397E66f3ByHvPGQ5nlAQ3wI7q+tLH+qPsoFUKcyfEbctuYvG
D0+9jPhvxAAQwc4hBhn+TXRXPkaaaI89iiaJoiF1//R8kqs8t3yxpxjEy0hs2nrx
tboZl91cO2fj8e2HvhbMs9v+j6oVTQIDAQABo4IBBTCCAQEwHQYDVR0OBBYEFIci
KzboRxhacra8qkU+xvRM4df7MIHRBgNVHSMEgckwgcaAFIciKzboRxhacra8qkU+
xvRM4df7oYGipIGfMIGcMQswCQYDVQQGEwJBWjENMAsGA1UECBMEQkFLVTEUMBIG
A1UEBxMLWWVuaVlhc2FtYWwxFDASBgNVBAoTC0FUTEluZm9UZWNoMQswCQYDVQQL
EwJJVDEXMBUGA1UEAxMOQVRMSW5mb1RlY2ggQ0ExLDAqBgkqhkiG9w0BCQEWHWph
bWFsLnNoYWh2ZXJkaXlldkBhdGx0ZWNoLmF6ggkAuxX95Bz9Xn4wDAYDVR0TBAUw
AwEB/zANBgkqhkiG9w0BAQUFAAOCAgEAT+K70oaUfXDEfSFmBTrppvbcGqoVsaEl
5NjMh206D5KWtERhKbP7id20sdt6YgqlPQWW3I3thVQ0L686rhbZ/cR6Vzj41cFI
EqCt4uqZrkoMcvPq82POnvrzKCauxv5kmZJhWQTB3WXMo0A4KnQqW6/HVzSmbQgC
QR6CqNTt1Z21a1RIQrR1CmqRankKC4yQBKbzDwBlXLHvjITdyhJlHXZxBcdXurMX
Uh7AsHOTxbHy4nbyB+Zz1nO37wza6FBeunIqJ/I5eKDcN1lyGELjDsEvrSUcbRRg
IenV9/D9LP4y2KghMkiuDn7vhY3IifCjxQg3JWIa5BdQ/lU1Accsx1i0/nyQtZF7
5NadlwoSOjEe2H6bwxhlngcItQyiC34HghNKUF16eYLlMEzGkP7UNLwQN32b3IiA
q9+HTP6TQoci43AoaA3NFaUjuKC3zHykesNS8QqOH7MVB4L38/piaGD/K8CsiZH+
QhkICaJJ7hx/Cfp3VUIKr9yxtAnC5QNbXr9QVCC+mwi/sH9laThPlm1Xd2tKdoZa
My/K6o5fZnZSpzOeFa9j6bRgF2tpbG3jxiWT00F9xUv5EtXZdfies5BRHa1FYGK4
yvVIA/ZJBSB/6CT8mnMjGJcn85CcRggOrOc7lQNmgFKw/YopPYyAKzjgi1EKtNm3
pmPKIhXPdvc=
—–END CERTIFICATE—–
</ca>
# TA key which is created in OpenVPN server
<tls-auth>
—–BEGIN OpenVPN Static key V1—–
7148f7b12478b04aee1445e18bb96509
b7f8d3c62d20ffb59241a13b714e951d
6e14ef9254097803e76b75e051866287
2cb6db296bbb2a7322b4d641d235b6e3
6426f086ecb6d0650ed61285a5e2a78b
f0f7b2352193c12cbff21ccc82054d00
a00a13d304d7d1365e955eeb30aece8f
15ca06b1c2f504de1ce03f9e955d17f6
a70db5635fd3d3fce914dc090a3f3d59
71db3e9955adf3797c50c50bbe0cbc4b
1aa8d3f363de18474eaeb0b7116edaba
00325fa6fd15da57ad10f9e81cf8d7f2
f1c16d95af55071365cefd8513c906af
e830c0c83f01eea30add98f734fd6011
f5c89c1822d516e0a0c3452c869a5940
929a37e3e064f307b17b8fbe8acb73c3
—–END OpenVPN Static key V1—–
</tls-auth>
# If you want to see the logs in detail just delete comment
#verb 3
Note: About how to create Domain groups, add users to this group and how to use OpenVPN client program you can read OpenVPN AD authentication with crypt article. Topology is same as there but, difference just operation system there FreeBSD and here Ubuntu.
After install Ubuntu server, update repository links and installed packets with kernel:
apt-get update # Update repository links
apt-get dist-upgrade # Upgrade kernel and installed packages
Install OpenVPN, OpenSSL, LDAP and RADIUS packages:
apt-get install openvpn easy-rsa openvpn-auth-radius openvpn-auth-radius-dbg
Install FreeRADIUS to the same server:
apt-get install freeradius freeradius-common freeradius-dbg freeradius-utils freeradius-ldap
Install ldap utilities for debugging:
apt-get install ldap-utils
cd /etc/openvpn # Go to the OpenVPN configuration folder
cat openvpn.conf # Configuration file will be as follows
plugin /usr/lib/openvpn/radiusplugin.so /etc/openvpn/radiusplugin.cnf
proto tcp
port 1194
dev tun
server 192.168.200.0 255.255.255.0
# About key generation you can read from Setup And Configure OpenVPN Server On CentOS 6.5 article.
ca /etc/openvpn/keys/keys/ca.crt
cert /etc/openvpn/keys/keys/openvpnserver.crt
client-cert-not-required
key /etc/openvpn/keys/keys/openvpnserver.key
dh /etc/openvpn/keys/keys/dh2048.pem
tls-auth /etc/openvpn/keys/keys/ta.key 0
persist-key
persist-tun
keepalive 10 60
# If we want write different configuration for each our clients, we must delete comments below.
#client-to-client
#client-config-dir /usr/local/etc/openvpn/ccd
push “route 10.99.2.0 255.255.255.0”
push “route 10.99.3.0 255.255.255.0”
push “route 10.99.12.0 255.255.255.0”
push “route 10.99.14.0 255.255.255.0”
push “route 10.99.17.0 255.255.255.0”
push “route 10.99.19.0 255.255.255.0”
push “route 192.168.10.0 255.255.255.0”
push “dhcp-option DNS 10.99.3.2”
push “dhcp-option DNS 10.99.3.3”
topology subnet
user root
group root
log-append /var/log/openvpn.log
The integration configuration file OpenVPN to FreeRADIUS will be as follows:
cat /etc/openvpn/radiusplugin.cnf # Configuration file to connect RADIUS
NAS-Identifier=OpenVpn
Service-Type=5
Framed-Protocol=1
NAS-Port-Type=5
NAS-IP-Address=127.0.0.1
OpenVPNConfig=/etc/openvpn/openvpn.conf # OpenVPN configuration file
overwriteccfiles=true
server
{
acctport=1813 # RADIUS accounting port
authport=1812 # RADIUS authentication port
name=127.0.0.1 # RADIUS IP
retry=1
wait=1
sharedsecret=freebsd # Key is used between FreeRADIUS and OpenVPN
}
Now let’s go to FreeRADIUS Configuration
To connect OpenVPN client to FreeRADIUS add it to FreeRADIUS client list (Configuration file will be as follows):
cat /etc/freeradius/clients.conf # Clients configuration file
client localhost {
ipaddr = 127.0.0.1 # OpenVPN server
secret = freebsd # Key is used between FreeRADIUS and OpenVPN
require_message_authenticator = no
shortname = localhost
nastype = other
}
FreeRADIUS configuration file will be as follows:
cat /etc/freeradius/radiusd.conf # FreeRADIUS configuration file
prefix = /usr
exec_prefix = /usr
sysconfdir = /etc
localstatedir = /var
sbindir = ${exec_prefix}/sbin
logdir = /var/log/freeradius
raddbdir = /etc/freeradius
radacctdir = ${logdir}/radacct
name = freeradius
confdir = ${raddbdir}
run_dir = ${localstatedir}/run/${name}
db_dir = ${raddbdir}
libdir = /usr/lib/freeradius
pidfile = ${run_dir}/${name}.pid
user = freerad
group = freerad
max_request_time = 30
cleanup_delay = 5
max_requests = 1024
listen {
type = auth
ipaddr = 127.0.0.1
port = 1812
}
listen {
ipaddr = 127.0.0.1
port = 1813
type = acct
}
hostname_lookups = no
allow_core_dumps = no
regular_expressions = yes
extended_expressions = yes
log {
destination = files
file = ${logdir}/radius.log
syslog_facility = daemon
stripped_names = no
auth = no
auth_badpass = no
auth_goodpass = no
}
checkrad = ${sbindir}/checkrad
security {
max_attributes = 200
reject_delay = 1
status_server = yes
}
proxy_requests = no
$INCLUDE proxy.conf
$INCLUDE clients.conf
thread pool {
start_servers = 5
max_servers = 32
min_spare_servers = 3
max_spare_servers = 10
max_requests_per_server = 0
}
modules {
$INCLUDE ${confdir}/modules/
$INCLUDE eap.conf
}
instantiate {
exec
expr
expiration
logintime
}
$INCLUDE policy.conf
$INCLUDE sites-enabled/
For checking communication between FreeRADIUS and OpenVPN add line below to the /etc/freeradius/users file(For test purpose I used username:vasif and password:freebsd):
“vasif” Cleartext-Password := “freebsd”
/etc/init.d/openvpn restart # Restart the OpenVPN daemon
/etc/init.d/freeradius restart # Restart the FreeRADIUS service
freeradius -fX # If you want to debug FreeRADIUS you can use this command
After that you must connect from Windows 8.1 desktop with OpenVPN client to server and get success. If fail you must start FreeRADIUS in debug mode. If everything is ok we are going FreeRADIUS MS LDAP integration.
To connect OpenVPN with AD users, we must integrate FreeRADIUS to MS LDAP. We must do follows:
cat /etc/freeradius/sites-enabled/default # Configure default virtual RADIUS
authorize {
files
ldap # If LDAP group will be
if (LDAP-Group == “OpenVpnFAUsers”) { # OpenVpnFAUsers then everything is OK.
ok
}
else {
reject # If not block
}
}
authenticate {
Auth-Type LDAP {
ldap # Either authentication will come from ldap
}
}
preacct {
preprocess
acct_unique
suffix
files
}
accounting {
detail
unix
radutmp
exec
attr_filter.accounting_response
}
session {
}
post-auth {
exec
}
pre-proxy {
}
post-proxy {
}
Configure LDAP module for filter Domain users:
cat /etc/freeradius/modules/ldap # Configuration LDAP module will be as follows
ldap {
server = “domain.lan”
identity = “CN=DCADM,CN=Users,DC=domain,DC=lan”
password = “DcP@$$f0rD0m”
basedn = “DC=domain,DC=lan”
filter = “(sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}})”
ldap_connections_number = 5
timeout = 4
timelimit = 3
net_timeout = 1
tls {
start_tls = no
}
dictionary_mapping = ${confdir}/ldap.attrmap
edir_account_policy_check = no
groupname_attribute = “cn”
groupmembership_filter = “(|(&(objectClass=GroupOfNames)(member=%{control:Ldap-UserDn}))(&(objectClass=GroupOfUniqueNames)(uniquemember=%{control:Ldap-UserDn})))”
groupmembership_attribute = “memberOf”
compare_check_items = no
do_xlat = yes
access_attr_used_for_allow = yes
chase_referrals = yes
rebind = yes
set_auth_type = yes
ldap_debug = 0
keepalive {
idle = 60
probes = 3
interval = 3
}
}
freeradius -fX # If everything is ok, in debug mode you must see logs as follow
[ldap] performing user authorization for jamal
[ldap] expand: %{Stripped-User-Name} ->
[ldap] … expanding second conditional
[ldap] expand: %{User-Name} -> jamal
[ldap] expand: (sAMAccountName=%{%{Stripped-User-Name}:-%{User-Name}}) -> (sAMAccountName=jamal)
[ldap] expand: DC=domain,DC=lan -> DC=domain,DC=lan
[ldap] ldap_get_conn: Checking Id: 0
[ldap] ldap_get_conn: Got Id: 0
[ldap] attempting LDAP reconnection
[ldap] (re)connect to domain.lan:389, authentication 0
[ldap] bind as CN=DCADM,CN=Users,DC=domain,DC=lan/DcP@$$f0rD0m to domain.lan:389
[ldap] waiting for bind result …
[ldap] Bind was successful
[ldap] Setting Auth-Type = LDAP
[ldap] user jamal authorized to use remote access
[ldap] ldap_release_conn: Release Id: 0
++[ldap] returns ok
++? if (LDAP-Group == “OpenVpnFAUsers”)
[ldap] Entering ldap_groupcmp()
expand: DC=domain,DC=lan -> DC=domain,DC=lan
expand: (|(&(objectClass=GroupOfNames)(member=%{control:Ldap-UserDn}))(&(objectClass=GroupOfUniqueNames)(uniquemember=%{control:Ldap-UserDn}))) -> (|(&(objectClass=GroupOfNames)(member=CN\3dJamal Shahverdiyev\2cOU\3dDOMAINTech Users\2cOU\3dDOMAINTech\2cDC\3ddomain\2cDC\3dlan))(&(objectClass=GroupOfUniqueNames)(uniquemember=CN\3dJamal Shahverdiyev\2cOU\3dDOMAINTech Users\2cOU\3dDOMAINTech\2cDC\3ddomain\2cDC\3dlan)))
[ldap] ldap_get_conn: Checking Id: 0
[ldap] ldap_get_conn: Got Id: 0
[ldap] performing search in DC=domain,DC=lan, with filter (&(cn=OpenVpnFAUsers)(|(&(objectClass=GroupOfNames)(member=CN\3dJamal Shahverdiyev\2cOU\3dDOMAINTech Users\2cOU\3dDOMAINTech\2cDC\3ddomain\2cDC\3dlan))(&(objectClass=GroupOfUniqueNames)(uniquemember=CN\3dJamal Shahverdiyev\2cOU\3dDOMAINTech Users\2cOU\3dDOMAINTech\2cDC\3ddomain\2cDC\3dlan))))
[ldap] performing search in CN=Jamal Shahverdiyev,OU=DOMAINTech Users,OU=DOMAINTech,DC=domain,DC=lan, with filter (objectclass=*)
[ldap] performing search in CN=OpenVpnFAUsers,OU=DOMAINTech Groups,OU=DOMAINTech,DC=domain,DC=lan, with filter (cn=OpenVpnFAUsers)
rlm_ldap::ldap_groupcmp: User found in group OpenVpnFAUsers
[ldap] ldap_release_conn: Release Id: 0
? Evaluating (LDAP-Group == “OpenVpnFAUsers”) -> TRUE
++? if (LDAP-Group == “OpenVpnFAUsers”) -> TRUE
++- entering if (LDAP-Group == “OpenVpnFAUsers”) {…}
+++[ok] returns ok
[ldap] user jamal authenticated succesfully
++[ldap] returns ok
Note: Do not forget clean /etc/freeradius/users file.
/etc/init.d/freeradius start # At the end restart the FreeRADIUS