Introduction
Advanced Policy Firewall or APF is iptable based firewall system which is a free distribution, this firewall is designed to meet today’s security based essential needs.The firewall is designed to be very informative and present the user with an easy to use follow process.
Features Highlight
The filters perfromed by APF can be catagourised in three parts
static rule based policy.
It define how firewall should handle certain traffic in specific conditions while giving access to certain port or adding some ip address as trusted one.
Connection based stateful policy
Firewall will identify valid/legitimated packets from the different types of connections and will allow only valid connections which are allowed in firewall rules and other will be rejected.
Sanity based policy
Can identify network attacks by screening or scrutinizing packets, it will discard and log any data which is considered as inappropriate.
Installation
It is recommended to have at least 2 LAN cards, 4 GB RAM, dual core processor and 1 GB free disk space to dedicate your system as APF firewall.
Update Ubuntu 15.10
# apt-get update
Download package
# wget http://www.rfxn.com/downloads/apf-current.tar.gz
Extract package
# tar -xvf apf-current.tar.gz
Extract and install package
# cd apf-9.7-2/ # ./install.sh
Sample output
Installing APF 9.7-2: Completed. Installation Details: Install path: /etc/apf/ Config path: /etc/apf/conf.apf Executable path: /usr/local/sbin/apf Other Details: Listening TCP ports: 53,631 Listening UDP ports: 53,68,631,5353,23566,47956 Note: These ports are not auto-configured; they are simply presented for information purposes. You must manually configure all port options.
Now have a look in /etc/apf/conf.apf
# The installation path of APF; this can be changed but it is not recommended. INSTALL_PATH="/etc/apf" # Untrusted Network interface(s); all traffic on defined interface will be # subject to all firewall rules. This should be your internet exposed # interfaces. Only one interface is accepted for each value. IFACE_IN="eth0" IFACE_OUT="eth0" # Trusted Network interface(s); all traffic on defined interface(s) will by-pass # ALL firewall rules, format is white space or comma separated list. IFACE_TRUSTED="eth0" # This option will allow for all status events to be displayed in real time on # the console as you use the firewall. Typically, APF used to operate silent # with all logging piped to $LOG_APF. The use of this option will not disable # the standard log file displayed by apf --status but rather compliment it. SET_VERBOSE="1"
Let us explain some of the important parameters which are important in this configuration file
IFACE_IN=”eth0″
IFACE_OUT=”eth0″
Interface in and interface out define which interface you will be using for firewall as inbound and outbound
DEVEL_MODE=”1″
Keep Developer mode as 1
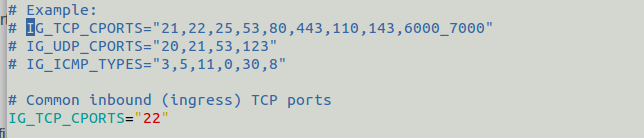
IG_TCP_CPORTS
Define allowed TCP ports
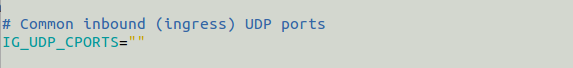
IG_UDP_CPORTS
Define allowed UDP ports
Command Examples
To start firewall
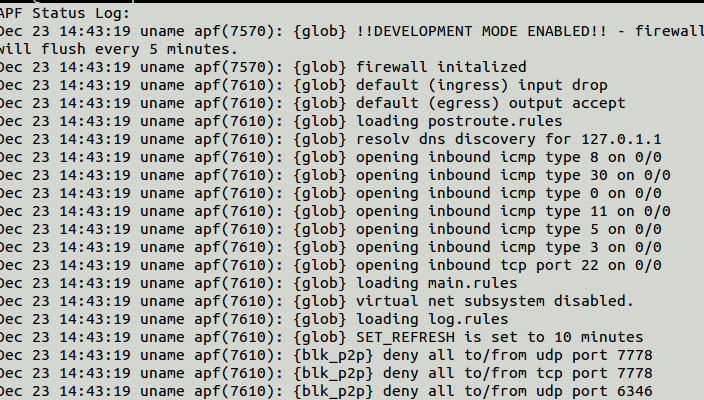
# apf -s
To stop firewall
# apf -f
Output
apf(7480): {glob} flushing & zeroing chain policies
apf(7480): {glob} firewall offline
To restart firewall
# apf -r
To dump current status of firewall on terminal
# apf -st
To deny some host
# apf -a 192.168.1.1
It will add IP ADDR to trusted address and entries goes to /etc/apf/allow_hosts.rules
# apf -d 192.168.1.1
Above command will add IP ADDR to deny, entries goes to /etc/apf/deny_hosts.rules
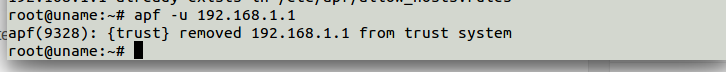
# apf -u 192.168.1.1
Remove entries either from trsuted or from deny hosts rules
Now your firewall is ready to work in an easy to use and deploy manner.
Have fun