Subgraph OS is a debian based operating system which is developed to keep security and privacy in mind. It is best suited for non technical users who want to enjoy the security of a Linux operating system without manually troubleshooting and adjusting the security settings of the system. To put into nutshell, Subgraph OS comes pre-configured with all important / required security settings and applications, all you need to do is to simply install it and feel the security and power of Linux. You don’t need to get your hands dirty with complex configuration files, firewall rules, security setting etc to make your system resilient, Subgraph OS is already a secure system for you. While we have been playing around this operating system, here are some of the features that we found noteworthy and should be taken into consideration while deciding on your Linux OS choice.
Mendatory Disk Encryption
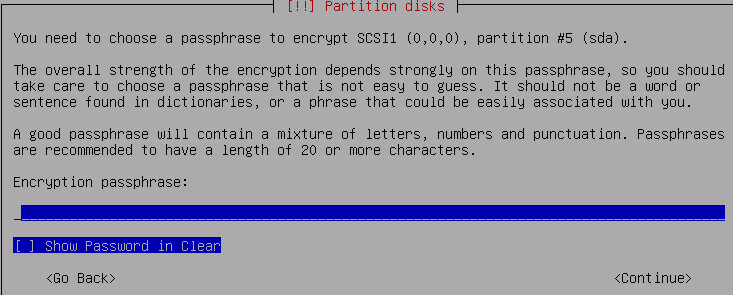
This is the very first feature which caught our attention during the installation process. Unlike many other Linux operating systems, Subgraph makes it mandatory to encrypt your disks using complex passphrase. Here is the screen you should be encountering during the installation process.
So even if you are the victim of theft or stolen laptop/computer, your hard disk(s) and data are pretty much secure and inaccessible for the bad guys.
Hardened Security
Subgraph comes with pretty good security settings; here is short list of what you will be seeing pre-configured after the installation of this operating system.
- Hardened Computing Platform
- Kernel Hardened with Grsecurity/PaX
- Application Network Policy
- Binary Integrity
- Package Security
Anonymized Browsing
Guess what, all traffic from your system is already routed via TOR network so it makes this hard for hackers/intruders to track down your original location and thus you are working as anonymous in this cruel world of hacking. Thus non-technical users can now enjoy the power of TOR without performing any additional configurations on their systems.
Icedove & CoyIM
The most important part of a daily life use of an operating system is email and chat. Subgraph comes with two important applications, Icedove and CoyIM to cater these needs of users. Icedove is the email client application which is based on Mozilla Thunderbird but comes with many secure features like default IMAPS , Enigmail, TorBirdy etc.
CoyIM is an internet messenger application which is written from scratch to overcome memory corruption vulnerabilities. It is a fast, reliable, secure XMPP based application and works flawlessly on Subgraph operating system.
Oz Security System
Oz is a security system for Subgraph, it isolates various running applications on the system in the way that if one application gets vulnerable, other running applications on same system should not be exploitable by hackers. It delimits the permissions applications have to the various part of the computer system so in this way any bad application can not lead to system wide malicious activities.
Conclusion
Hope you enjoyed this article! Subgraph is still in alpha phases, but under consistent development and we hope to see it more stable, mature and secure in the near future. It is available in 64bit architecture only and can even run on systems having 1 GB of memory and 20 GB of free disk space. If you are using any other security focused operating system like Subgraph, please feel free to share your experience in comments section. Thank you!!