Introduction
External and internal attackers day after day are menacing your networks. Many intelligent methods are discovered in order to get access and damage your server. Currently, the Sun Java system application server can’t be as beneficial as it was previously since the tactics used by those attackers are being more dangerous nowadays.
So you need to have a background knowledge of some basic security practices to more protect your server and your personal information. So we will list the most important steps to follow to strengthen your security.
Use a strong firewall
As Cloutier, Chief Security Officer for ADP says: “in order to have a properly protected network, firewalls are a must”. In fact, firewalls enable you to protect your network by controlling the internet traffic coming on and what services are exposed to it.
The services are categorized into three groups so their user’s access aren’t the same. The first group is the public services which are accessed by everyone on the internet. The second is the private services which have some restrictions on the number of the users. They can be accessed just by a specific group of authorized accounts such as the database control panel. And the last one is the internal services. As its name means it is internal no exposition on the outside world is made.
Firewalls enable you to control the ability to access to your server depending on which group of the three listed above fits your situation. You can give access to everyone due to the public services while this permission can be restricted using the private services and can be completely inaccessible to the outside world.
Currently, many types of firewalls are available for Linux operating systems. Generally, you will just need to set up the firewall for few minutes during your first setup of your servers or every changes can occurred on them. I think that few minutes is nothing regarding the importance to use this tool to strengthen the protection of your servers.
Don’t be lazy and don’t neglect the huge benefit you can gain while using the firewall on your computer to control the accessibility to your servers.
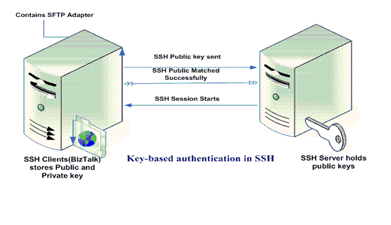
SSH keys
The second method to use in order to more protect your servers is the SSH keys. It is an alternative of the password based logins can be used to authenticate an SSH server. As a pair of cryptographic keys either public or private are just create for you and your systems protection. As their name mean, the public can be shared by different users while the public one is just for the concerned user.
The configuration of the SSH key is very simple, you just need to save the user’s public key on your server within a specific director. Regarding the private key you need to have a proof justify your possession of this private key since it is accessibility is very secure. While the verification of the availability of the private key with the user, no password will be demanded, just connect directly to the asked directory.
With SSH key, the attacker will spend very long time trying to find the right demanded password, since SSH keys have a huge number of bits of data than a simple password. They are the easiest tool to set up and the most recommended one to use while logging on the Linux or Unix server. The transfer of the public keys can be made in the fastest way you can imagine. Just few minutes and the selected users may have the possibility to log in and use the considered server. So you have now the last decision either to use this type of authentication or use the standard method with password.
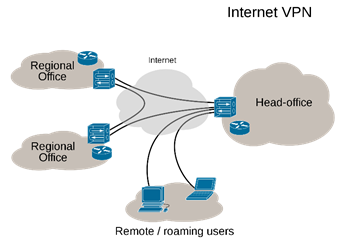
VPNs and Private Networking
The private network is a kind of network that is based on a private IP address space. It can be used for house, office and company local area networks known as LANs. They are considered as private since no IP packets addressed can be transmitted through the public internet. While the VPN, Virtual Private Network, give you the possibility to create connections between different computers presented in different locations.
The VPN is the adequate method for more secure connections between different computers. You can communicate, work and share information together in a more protected way. Your communications will be fully private and secure you have not to worry about this issue of communications protection.
Within a datacenter, while using the private networks is very easy with VPN since in a data center different private networks share the same space and use the same network. But it is required to install and configure each server on VPN, also applications must be configured to have accessibility to the VPN tunnel.
Public Key Infrastructure and SSL/TLS Encryption
If you want to create, manage, and validate certificates for identifying users and encrypting communications, so you have to use Public Key Infrastructure known as KPI. Furthermore, we can mention the SSL and TLS certificates which can be used to authenticate different systems to specific user, and to make encrypted communications.
So you can verify the identity of each member within your infrastructure and encrypt their traffic due to the ability to establish certificate authority and manage them depending on your servers. Which helps you to prevent every interruption in the middle can be occurred by an attacker.
Each certificate made and signed by the concerned authorities, it will be directly trusted by others. While encrypting your system with the SSL/TLS encryption, no need for using a VPN tunnel.
Isolated Execution
Isolated Execution is a software addressed for providing more security through isolation concept. It provides a contained environment where mal-ware have the possibility to run without affecting the whole system, instead of stopping them or avoiding their insertion in the user’s machine.
The isolated execution enable users to limit any kind of damage may be caused by malware through sandboxing, to restrict the speed and distribution of virus due to its containment and it also leads to decrease the human error which may cause attack. Each user’s applications and infrastructure have a specific level of isolation.
To add, that using the isolation execution you will benefit by zero day attacks which is the wish of every computer user.
Conclusion
In this article, different methods were outlined above, which aren’t the all existed ones nowadays, just some of them to help you improve the security of your systems. But if you have heard somewhere about other tool, you think that it is also important so please share this information with your fellow readers by leaving a comment to make our work more helpful. Of course we can add this to the description made in our article.