In today’s article we will guide you through the process of installing mod_security with the OWASP (Open Web Application Security Project) core rule set on a CentOS 7 from source.
ModSecurity is a web application firewall engine that provides very little protection on its own. In order to become useful, ModSecurity must be configured with rules. In order to enable users to take full advantage of ModSecurity out of the box, Trustwave’s SpiderLabs created the OWASP ModSecurity Core Rule Set (CRS) Project. Unlike intrusion detection and prevention systems, which rely on signatures specific to known vulnerabilities, the CRS provides generic protection from unknown vulnerabilities often found in web applications, which are in most cases custom coded.
Prerequisites
Log in to your your server as user “root” user credentials and make sure that all packages are up to date. You can make use of below command to update your CentOS 7 server.
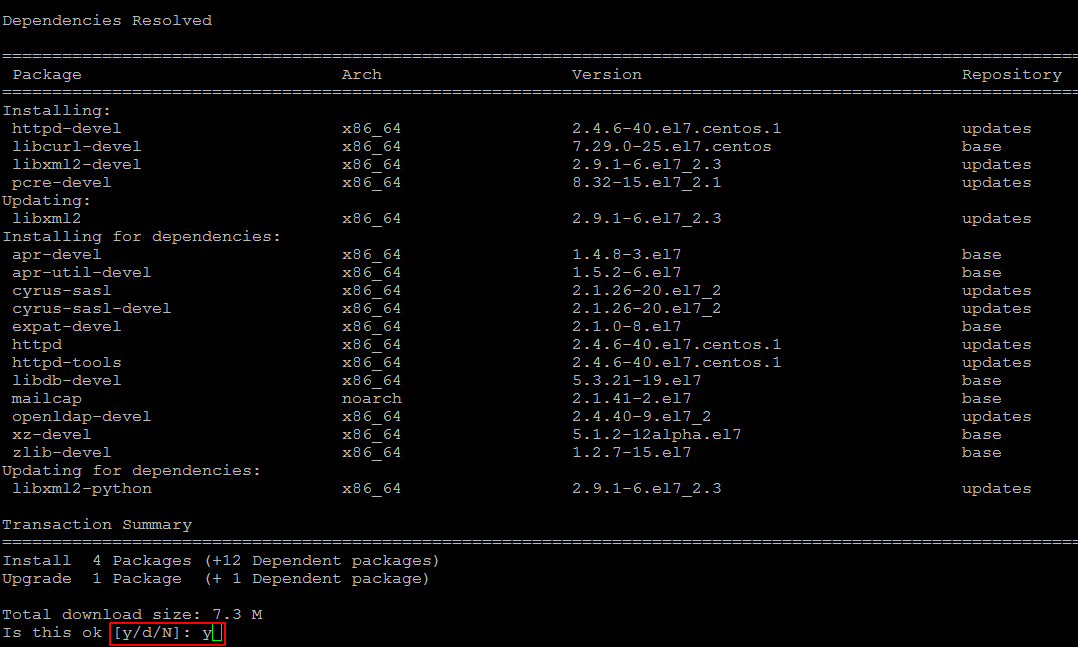
After system update install the following dependencies as ModSecurity 2.x works only with Apache 2.0.x or higher. Let’s run below command to install apache and its other dependencies as shown below.
Installing mod_security
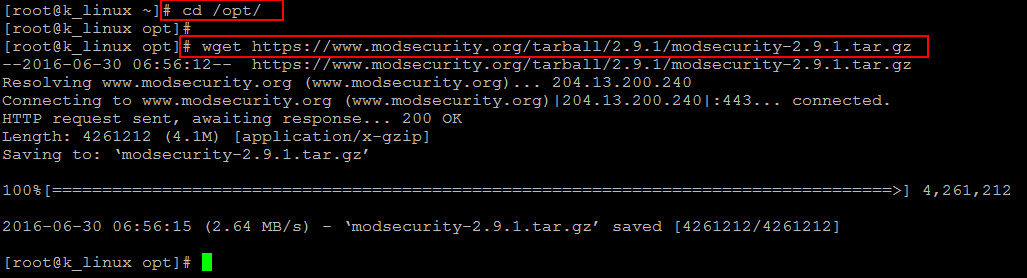
Get the ‘mod_security’ source package to install on your server from their official website link .mod_security can be installed in most web servers like Nginx, Apache and even Microsoft IIS. But in this tutorial will cover only on a server running Apache.
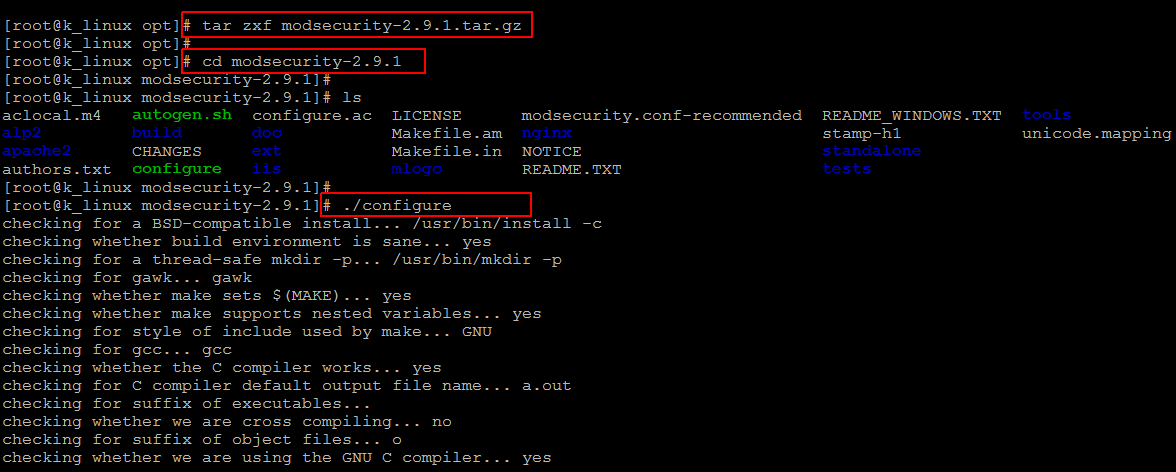
Extract the downloaded archive and change the current working directory to the newly extracted directory using below commands.
Now, using below commands configure, compile and install mod_security from the source code as shown shown.
Configure mod_security
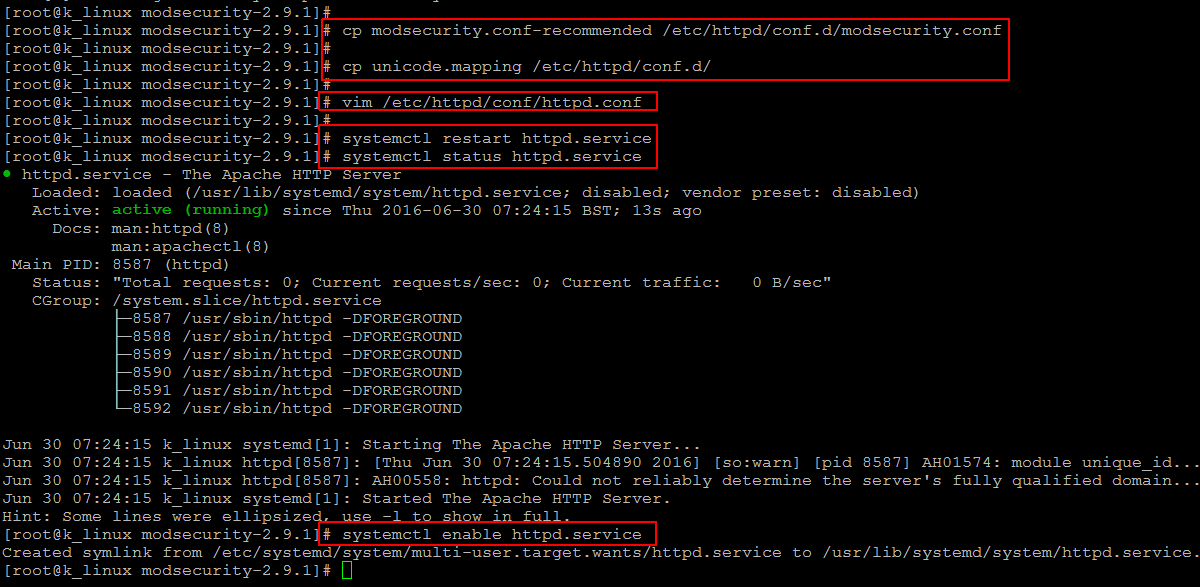
After installation setup of mod_security, copy recommended configuration files.
Now we need to configure the Apache web server . Open the web server configuration file and add the following lines in it.
LoadModule unique_id_module modules/mod_unique_id.so
Save the changes using ‘:wq!’ and restart Apache services.
# systemctl status httpd.service
# systemctl enable httpd.service
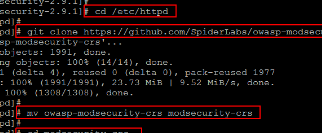
Installing OWASP
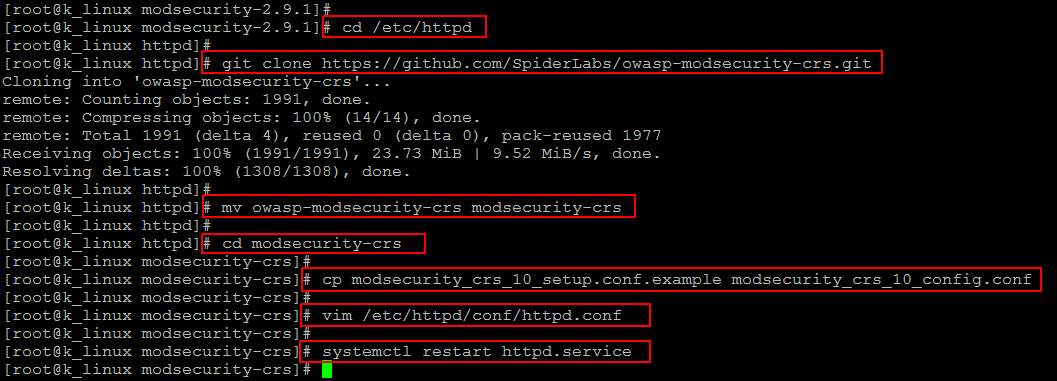
Now we will install OWSAP CRS to be integrated with Apache’s ModSecurity. Use below commands to download and configure OWASP (Open Web Application Security Project) core rule set for a base configuration.
Now once again open the Apache configuration file to add the following lines at the end.
LoadModule unique_id_module modules/mod_unique_id.so
So now you’ve installed Mod_Security and OWASP-CRS, it’s time to restart Apache service so the module can be loaded along with its rules.
Enjoy some basic necessary protection on your Linux CentOS 7 Apache server. It gives you couple of other advantages like below.
Real-time Blacklist Lookups: utilizes 3rd Party IP Reputation
Web-based Malware Detection: identifies malicious web content by check against the Google Safe Browsing API.
Identification of Application Defects: alerts on application misconfigurations.
HTTP Denial of Service Protections: defense against HTTP Flooding and Slow HTTP DoS Attacks.
Tracking Sensitive Data: Tracks Credit Card usage and blocks leakages.
Trojan Protection: Detecting access to Trojans horses.
Integration with AV Scanning for File Uploads – detects malicious files uploaded through the web application.
Error Detection and Hiding: Disguising error messages sent by the server.
Common Web Attacks Protection: detecting common web application security attack.
Automation Detection: Detecting bots, crawlers, scanners and other surface malicious activity.
HTTP Protection: detecting violations of the HTTP protocol and a locally defined usage policy.
Conclusion
mod_security is basically used to protect and monitor real time HTTP traffic and web applications from brute fore attacks and it also acts as intrusion detection and prevention system for web applications. In order to become useful, ModSecurity must be configured with rules which we can then use OWASP (Open Web Application Security Project) which is a Core Rules Set (CRS) for mod_security base configuration. Thank you for reading this and I hope you find this article useful.