 What is Base64 Encoding?
What is Base64 Encoding?
Base64 is a binary-to-text encoding scheme that represents binary data in an ASCII string format. It’s designed to carry data stored in binary formats across channels that only reliably support text content. Base64 decoding is the process of converting this encoded ASCII text back into its original binary form. This guide will show you how to decode base64
Why Use Base64 Encoding?
Base64 encoding is used for several reasons:
- To ensure safe transmission of binary data
- To store binary data in systems that only support text
- To embed binary data in text-based formats like JSON or XML
- To obfuscate data (though it’s not a secure form of encryption)
Understanding the Base64 Alphabet
The Base64 alphabet consists of:
- 26 uppercase letters (A-Z)
- 26 lowercase letters (a-z)
- 10 numbers (0-9)
- 2 additional characters (+ and /)
- = for padding
This creates a 64-character alphabet, hence the name “Base64”.
How to Decode Base64
Base64 decoding involves these steps:
- Convert each Base64 character to its 6-bit binary value
- Concatenate these 6-bit values
- Split the binary string into 8-bit chunks
- Convert each 8-bit chunk to its corresponding ASCII character
Methods to Decode Base64 Strings
Using Online Tools
Many websites offer free Base64 decoding tools. Simply paste your Base64 string and click “Decode”.
Using Command Line Tools
Most Unix-like systems include base64 as a built-in command:
Programmatic Decoding
Most programming languages have built-in functions or libraries for Base64 decoding. Here’s a Python example:
encoded = “SGVsbG8gV29ybGQh”
decoded = base64.b64decode(encoded).decode(‘utf-8’)
print(decoded) # Outputs: Hello World!
Common Use Cases for Decoding Base64
- Email Attachments: MIME uses Base64 for binary attachments
- Image Embedding: Decoding Base64 strings to display images in web applications
- API Communication: Decoding Base64-encoded data received from web services
- Data Storage: Retrieving binary data stored as Base64 in databases
- Authentication: Decoding Base64-encoded credentials in basic authentication
Potential Issues with Base64 Decoding
- Padding Errors: Incorrect padding can lead to decoding failures
- Character Set Issues: Non-standard Base64 alphabets can cause problems
- Increased Data Size: Base64 encoding increases data size by about 33%
- Security Misconceptions: Base64 is not encryption and doesn’t provide security
Best Practices for Handling Base64 Encoded Data
- Validate Input: Ensure the input string is valid Base64 before decoding
- Handle Errors Gracefully: Implement proper error handling for decoding failures
- Consider Data Size: Be aware of the increased size of Base64 encoded data
- Use Standard Libraries: Rely on well-tested libraries for encoding/decoding
- Secure Transmission: Use HTTPS when transmitting Base64 encoded sensitive data
- Don’t Rely on Obscurity: Remember that Base64 is easily reversible
Base64 Decoding in Different Programming Languages
JavaScript
Python
base64<span class="token">.</span>b64decode<span class="token">(</span><span class="token">"SGVsbG8gV29ybGQh"</span><span class="token">)</span><span class="token">.</span>decode<span class="token">(</span><span class="token">'utf-8'</span><span class="token">)</span>
PHP
Java
<span class="token">new</span> <span class="token">String</span><span class="token">(</span><span class="token">Base64</span><span class="token">.</span><span class="token">getDecoder</span><span class="token">(</span><span class="token">)</span><span class="token">.</span><span class="token">decode</span><span class="token">(</span><span class="token">"SGVsbG8gV29ybGQh"</span><span class="token">)</span><span class="token">)</span><span class="token">;</span>
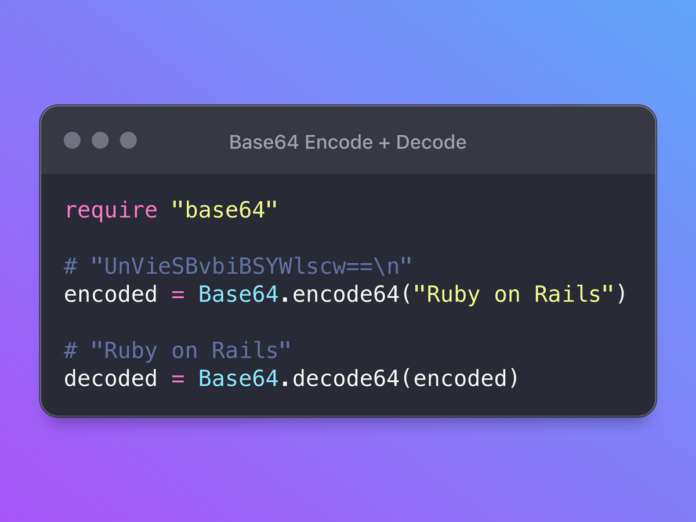
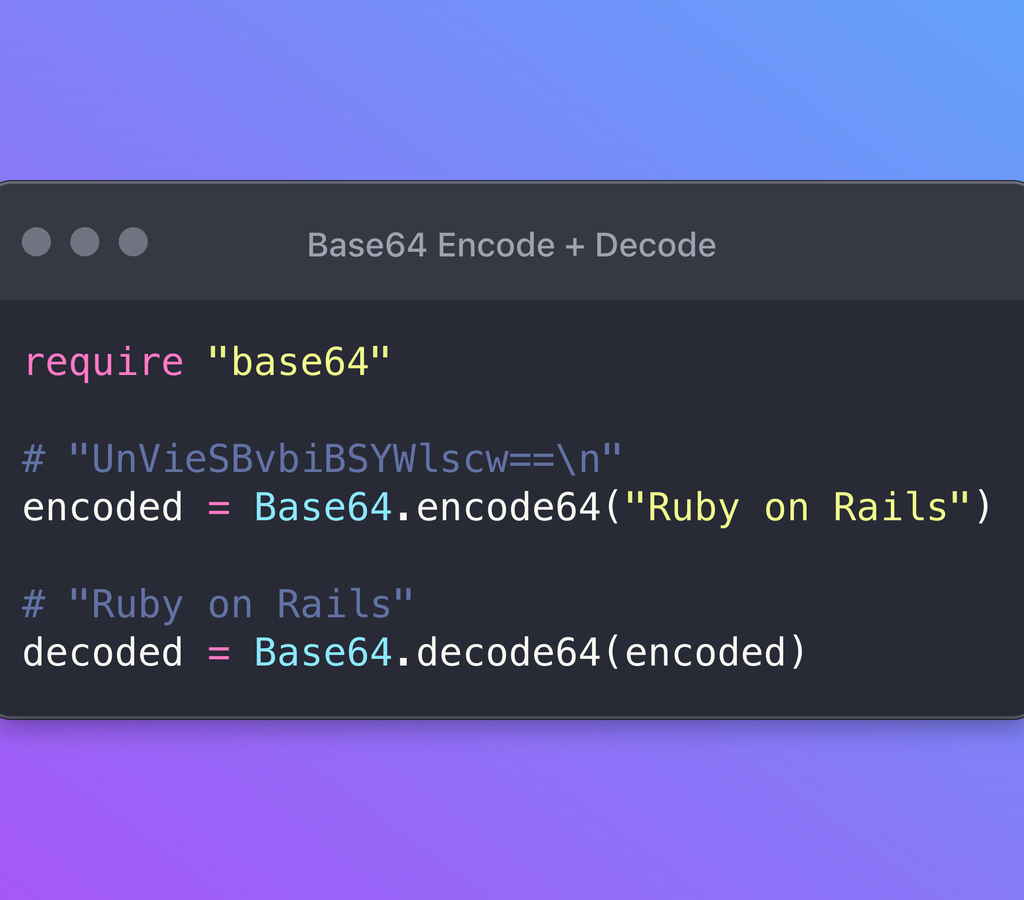
Ruby
Base64<span class="token">.</span>decode64<span class="token">(</span><span class="token string-literal">"SGVsbG8gV29ybGQh"</span><span class="token">)</span>
Understanding Base64 decoding and following these best practices, you can effectively work with Base64 encoded data in your applications. Remember, while Base64 encoding can be useful for data transmission and storage, it’s not a secure method for protecting sensitive information.
Similar Articles from Unixmen