Introduction to chapter 6 of module-1 of RHCSA
In this last chapter of module-1 of RHCSA we will discuss about File permissions, SUID, SGID, sticky bit, acl, nmcli, and nmtui which are a very important aspect of RHCSA examination. Till date we have discussed basics of RHCSA certificate examination, basic command lines which are required for Red Hat Administration, user and group management, vim file editor and other file management tools, you can go through following links to have a look on previously published articles of the series:
http://unixmen.com/everything-know-rhcsa-certification/
http://unixmen.com/basics-must-know-rhcsa-exam-preparation/
http://unixmen.com/learn-man-vim-editor-file-globbing-rhcsa/
http://unixmen.com/learn-file-management-commnad-line-required-rhcsa/
http://unixmen.com/hard-soft-links-user-group-management-rhcsa/
For today we will cover following topics.
- Linux file permissions using basic permissions, specials permissions with SUID, SGID, Sticky bit and ACL in Red hat Linux.
- Managing network services configuration in Red hat Linux using nmcli and nmtui.
- Secured remote access via ssh.
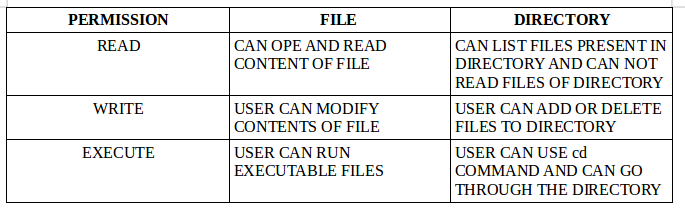
Managing basic file permissions in Red Hat Linux
User could have read, write or execute permission on any directory or file, additionally there are some special permissions i.e. SUID, SGID or ACLs. Have a look on various aspects of file or directory permissions.
Go to /home directory and list contents
# cd /home && ls -l
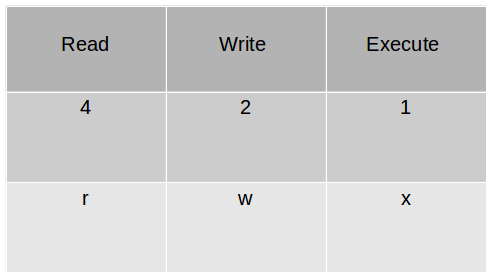
Latter d means it is a directly, then we have rwx on first three positions which means user have read (r), write (w) and execute (x) permission with the directory, next three -(minus) shows that group do not have any permissions and further next three – (minus) spaces shows that there no permission for others which means rest of the world which is not the part of this group. These read,write and execute permissions can also be denominated by numerical values of 4 (read),2(write) and 1(execute). These permission can be applied for user, group and other or ugo.
Create a file and change its permissions, use chmod command to change permissions.
# touch examplefile # chmod 754 examplefile
The above command will set read, write and execute permissions for user (4+2+1), read and execute permission (4+1) for group and read (4) for others.
Let us change permissions for by another method using rwx
Remove execute permission from group for examplefile
# chmod g-x examplefile
Have a look
# ls -l examplefile -rw-r--r--. 1 root root 0 May 31 03:57 examplefile
Add execute permissions to user group and others
# chmod ugo+x examplefile
Have a look
# ls -l examplefile -rwxr-xr-x. 1 root root 0 May 31 03:57 examplefile
It is recommended to use digital method for changing file permissions as this method is simple and less confusing.
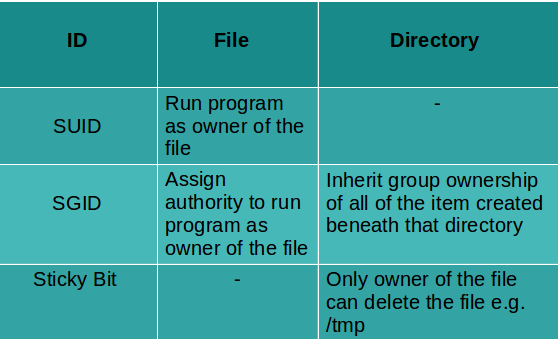
Understanding special permissions using SUID, SGID and sticky bit
Sometimes files required execute permissions for users which are not the members of the owner’s group, in that case you will be required to provide special execute permissions. When SUID is set then user can run any program like owner of the program. SUID means set user ID and SGID means set group ID.
SUID have a value of 4 or use u+s. SGID has value of 2 or use g+s similarly sticky bit has a value of 1 or use +t to apply the value.
Managing SUID in Red Hat Linux
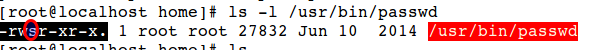
Let us have a look in passwd command program which is executable by all users, you can notice a small ‘s’ in permission of the file, due to SUID set for the program, every user can change their own passwd by executing that passwd file.
Create some shell script as root.
# vim um.sh
Put some contents in that file
#! /bin/bash echo "hi do you want to list contents of /root?" read rm -rf /
Now this is a very dangerous file, give execute permission to the file.
# chmod +x um.sh
Run that file with some non root user, file will be executed but there will be permission issue.
Let us assign special permission for that file using suid, now user can run that file like owner, which can give some serious damage.
# chmod +s um.sh
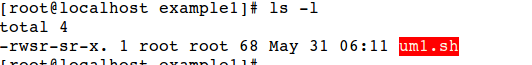
Have a look to the permissions now
The red highlighted area indicate that the file is possessed with suid.
Important: The above script is for example only, do not run this script on your system at all, you are never recommended to use SUID, it is never used in routine administration life, avoid to give special permission using SUID. Set user id is only used in some of system files like passwd command.
Managing SGID in Red Hat Linux
A special permission given to the user for a directory, it is a temporary permission which give rights of group membership so that the other user can use that file like member of the owner’s group.
Example
Create a directory named /datashare
# mdkir /datashare
Create a new user named guest1
# useradd gst1
Create a group sales
# groupadd sales
Change group ownership of /datashare to sales group
# chgrp sales /datashare
Now, add user guest1 to group sales
# usermod -G guest1,sales guest1
Create a new file in /datashare directory as user guest1
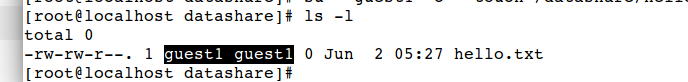
# su - guest1 -c "touch /datashare/hi.txt"
Have a look in permissions, this file belongs to group guest1
Now change group id for the folder /datashare
# chown g+s /datashare
or
# chown 2775 /datashare
Again create some file in /datashare
# su - guest1 -c "touch /datashare/echo.txt"
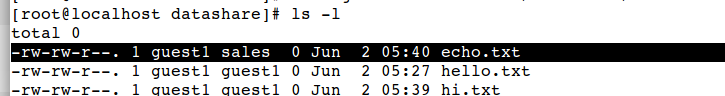
Have a look on ownership again
You can see that ownership of file is changed to group sales.
Using Sticky bit in Red Hat Linux 7
Sticky bit is a permission bit that will only let the owner of the directory to delete or rename the contents. /tmp comes with a sticky bit by default so that all of the user can access that directory, but file created by one user can not be deleted by some another user. Have a look
# ls -ld /tmp
You can see that although /tmp have read, write and execute permissions for all but sticky bit is enabled which is represent by t so that only owner of the file can delete or rename that file.
Apply sticky bit to some new folder with full permissions to all.
# mkdir /example && chmod 777 /example
Apply sticky bit with chmod command adding +t to apply sticky bit.
# chmod +t /example
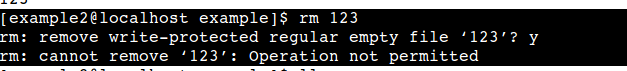
Create some file with user example1. and try to delete this file logging in with user example2,
This is clear in above example that only owner of the file can delete or rename the file.
Managing ACL in Red Hat Linux
Access control list is used to give permissions to more then one user or group on a directory, using acl you can give less permission to one group for a file and more permission to anther file for the same file.
or you can specify default permissions for newly created file/directories, for example you can define that every newly created file will be having right permission.
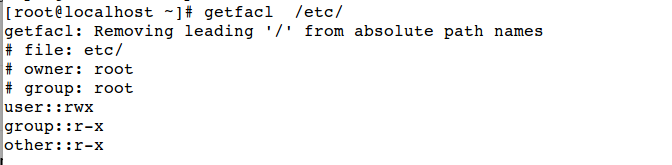
To see current access control settings use
# getfacl
Create a new directory
# mkdir acl
Let us give rw permission to group sales for that directory using acl.
With the help of setfacl command acl is defined, -R for recursive option, -m to modify default permissions. g for group and define what permisson you have to assign.
# setfacl -R -m g:marketing:rw acl/
To set default acl for all of the files or directories which will be created in that directory we need to define default acl, add d before g to apply these settings as default.
# setfacl -m d:g:marketing:rw acl/
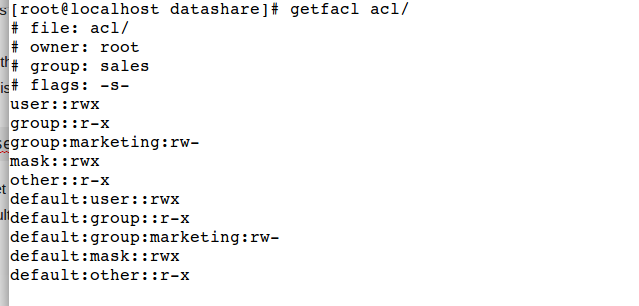
Have a look on these modified permissions
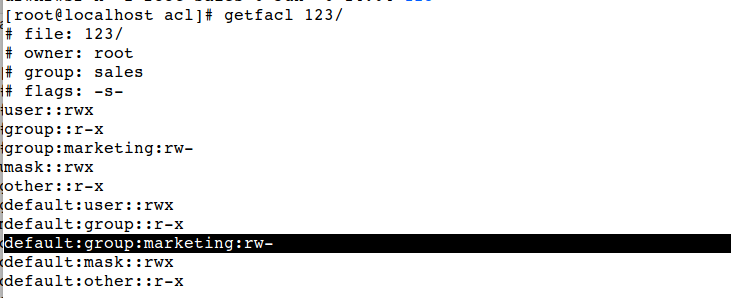
You can notice that in above example default settings and group ‘marketing’ permissions are set to read and write.
Create a new directory under acl/
# mkdir /acl/123
Have a look on permissions, you can see that permissions are same as of parent directory.
# getfacl
Manage and configure networking in Red Hat Linux
There are certain tools with the help of which network services can be handled in red hat Linux 7.
Manage ip addressing using ip command in Red Hat Linux
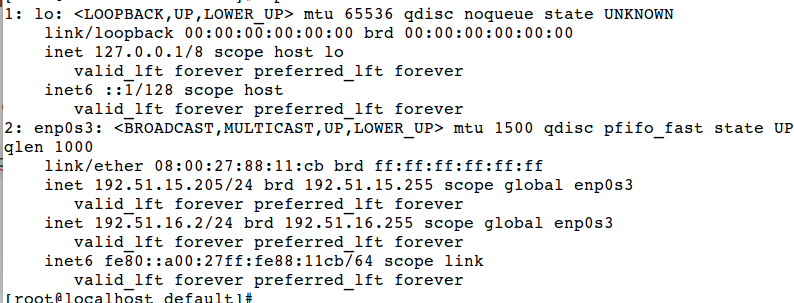
Show current address
# ip addr show
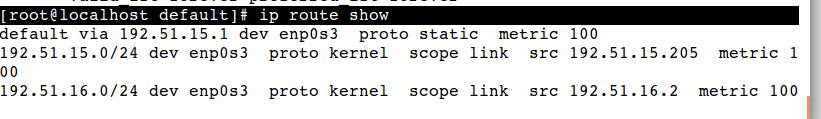
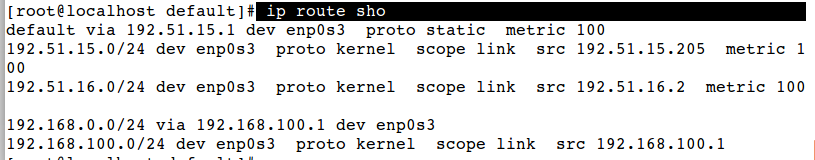
Show default gateway or routing table
# ip route show
Add ip address using ip tool
add -add a new ip
dev -device name
enp0s3- device name
# ip addr add dev enp0s3 192.168.100.1/24
Create a new gateway
# ip route add 192.168.0.0/24 via 192.168.100.1
Have a look
But if server is rebooted, all settings will be vanished, so you are required to save those settings.
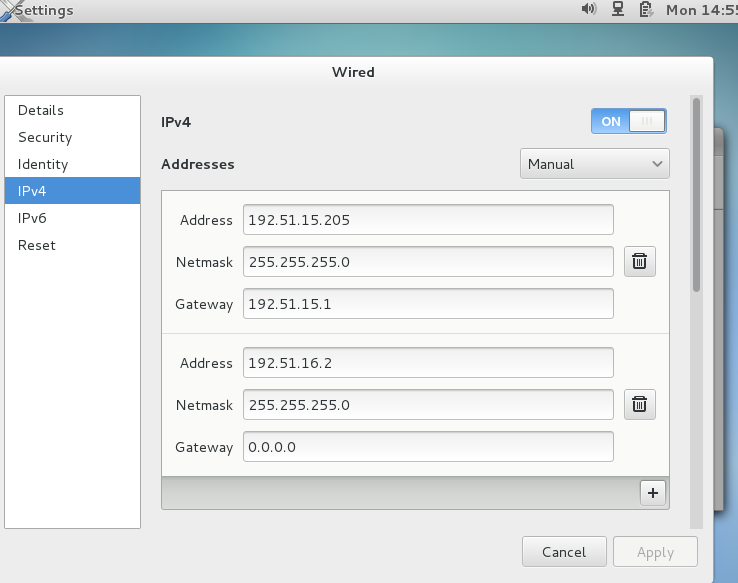
Storing IP configuration in Red Hat Linux
Best method is to use GUI interface to manage IP addressing in Red Hat Linux 7, click on network icon, go to setting and define ip address.
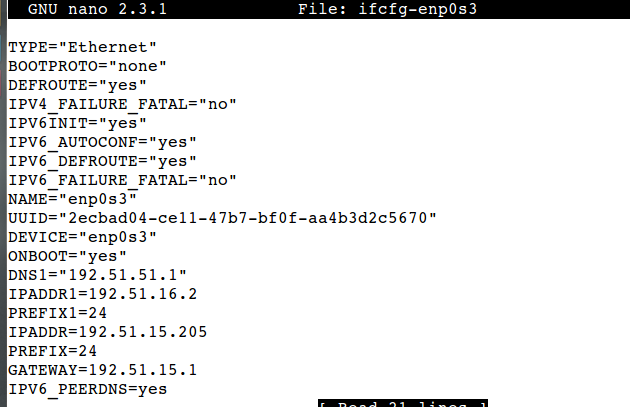
Apply settings, now network setting will be stored as permanent in your network script under /etc/sysconfig/network-scripts/ directory
# cd /etc/sysconfig/network-scripts/
Have a look in your network script
# nano ifcfg-enp0s3
Using nmcli and nmtui in Red Hat Linux 7
List working connection
# nmcli connection show NAME UUID TYPE DEVICE enp0s3 2ecbad04-ce11-47b7-bf0f-aa4b3d2c5670 802-3-ethernet enp0s3
Add a new connection with nmcli
Use
add – to add connection
con-name – define name of new connection
ifname – name of interface
type – define interface type
ip4 – assign i paddress
you can use <TAB> to auto complete the command
# nmcli connection add con-name unixmen ifname enp0s3 type ethernet ip4 192.51.10.1/24
Show connections
# nmcli connection show
New connection is listed
A new script will be generated in /etc/sysconfig/network-scripts/.
Put down this unixmen connection
# nmcli connection down unixmen
Up this connection
# nmcli connection up unixmen
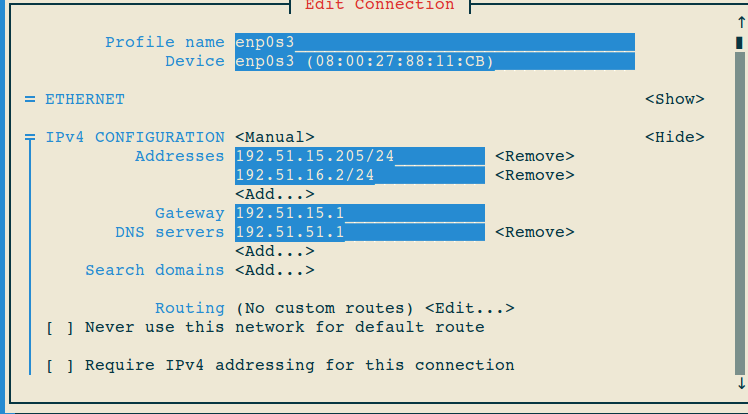
Another method to configure network interface in red hat 7 is nmtui
# nmtui
Edit connection you wants to configure
Save configurations
# systemctl restart NetworkManager
Display hostname
# hostnamectl status
Securing remote services with ssh in Red Hat Linux 7
Secure shell allow user to login to server remotely in a secure way.
Login to server using ssh
# ssh localhost
When you login first time using ssh, a key fingerprint is generated which is stored in target machine permanently in .ssh/known_hosts under home directory.
# cat ~/.ssh/known_hosts
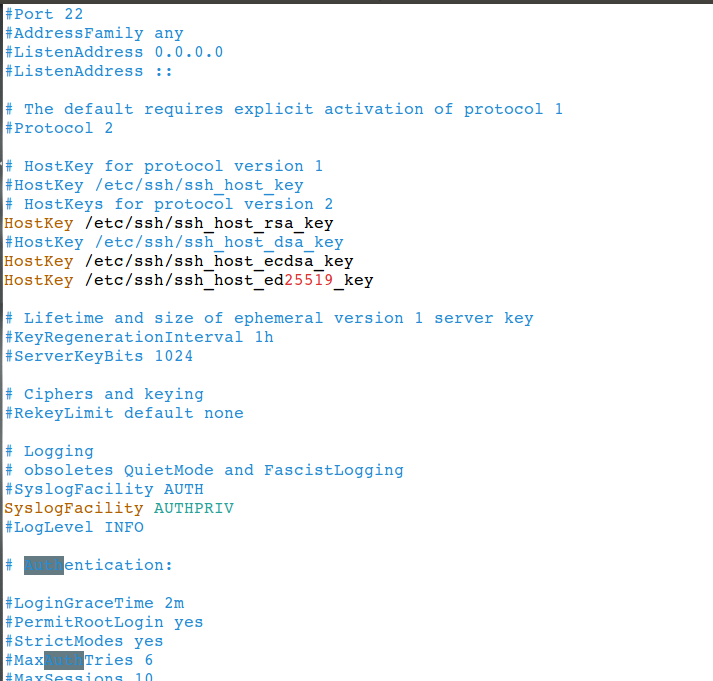
ssh configuration settings are stored under /etc/ssh/sshd_config file, have a look
# nano /etc/ssh/sshd_config
Default port for ssh is 22, but you can change that port via configuration file, to disable root login change PermitRootLogin settings to no.
When a client connect to ssh server, server send its identity to client via sending /etc/ssh/ssh_host.pub file to the connecting client which is a shred public key to build a trusted connection.
Connect to remote host using key based authentication instead of using password.
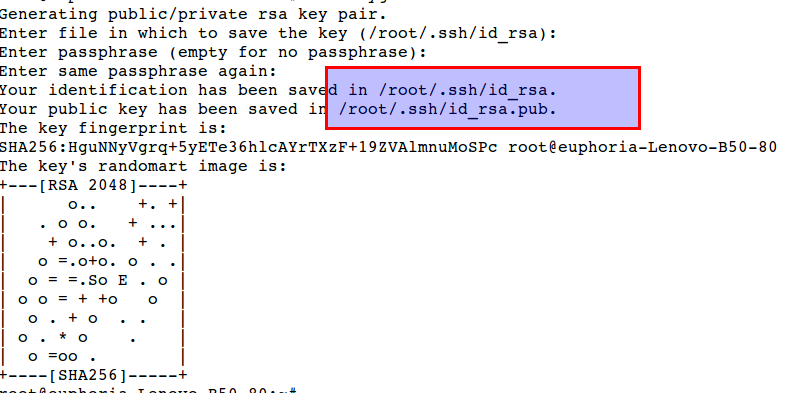
In key based authentication we use private key which is stored locally and public key which is shared with remote host. We need to generate those keys first using following command, left password option as empty.
# ssh-keygen
Notice that id.rsa and id.pub keys are generated which are stored in .ssh under home directory.
Copy public key with target host.
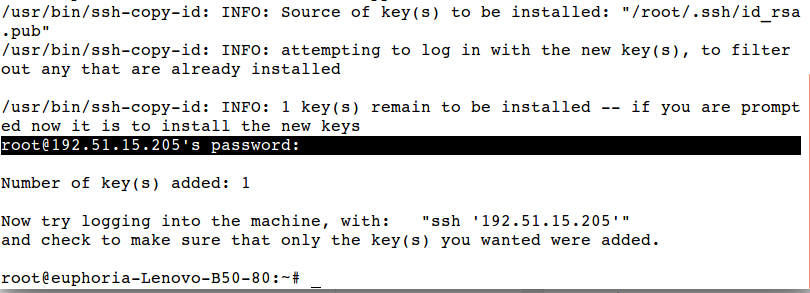
# ssh-copy-id 192.51.15.205
Give password of the host machine when prompted.
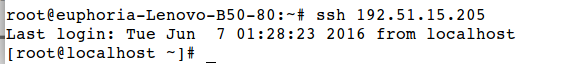
Now ssh the 192.51.15.205 machine, it will not ask for any password.
This is how we can manage remote services with trusted key based remote access or password based authentication based access.
Conclusion
Candidate should be able to manage file permissions, special file permissions using SGID, SUID, sticky bits, candidate can manage advanced file permissions using acl. chmod, getfacl, setfacl are the important commands which must be memorised for RHCSA exam preparation, think twice before defining file permissions, never use SGID in routine Linux administration practices, this was the last chapter of Module-1 of RHCSA examination preparation guide. From next chapter we will continue with Module-2 of RHCSA.