What if you come to know that the website you just visited has taken all the confidential data from your laptop/ server / PC? Well it happens and most of the times you come to know when the person has used that information somewhere else. In this article we will discuss Clickjacking and SlowLoris attacks and will learn how can we fix or prevent them on our Centos 7 system.
Clickjacking
It is a technique in which the person makes you click on any part of the web page but in actual you are clicking something which is hidden behind it and in other words the image you are seeing is not the actual image, as a bigger image is hidden behind it. There is no such indication of such an attack as it is presented in a very sophisticated way. As soon as you click somewhere on the page it performs a per defined backend action on the hidden page/image and somehow your confidentiality is compromised due to the execution of the scripts which hackers/intruders used. There are many examples like you can see on some websites that +1 Google plus sign, sharing the news or anything on Twitter, Following someone on Facebook and other Google AdSense clicks
SlowLoris
SlowLoris attacks is a kind of DOS (Denial Of Service) attack in which one webserver attacks on the other webserver and also effects on other services running on the destination system. It’s also known as Slow HTTP Denial of Service Attack. It is very common as in the backend of attack what it does is to use all the resources of the recipient webserver and chokes it up and doesn’t allow it to use any of the resource and as soon the resources fill up, your webserver crashes down and it can cause outages to the critical applications/websites. Now the question arises how all the resources can be utilized by this naughty fashion? It’s very easy and simple; you open a connection and don’t release and you keep opening connections and stop releasing them and a time will come when the connections on the system will reach maximum allowed limit. No new connections will be entertained and nor the old ones will be released. This will create a deadlock as the legitimate users who want to visit the website will not be entertained and they will find system in unusable state.
Fixing Clickjacking
As we have understood the basics of these attack, lets see how to fix these two on Centos7 Apache webserver. First we will see how we can minimize the Clickjacking attack on our system. Most important thing is to know is if your server is vulnerable at the moment or not. First of all we will check if webserver is running or not by the following command.
“X-Frame” Options parameter is used in Apache server to prevent people from using Clickjacking attack. Most important thing is to understand what this parameter does in the background. As discussed above that hacker attack by hiding the content behind any image, frame or any other form of page. By enabling this parameter on your we server, the web page’s ability to open in a Frame will be disabled as the hidden layer will not be activated which can be used as an attack to get personal information. We can check this by the following command.
Replace http://192.168.0.119/ with your own system’s IP address.
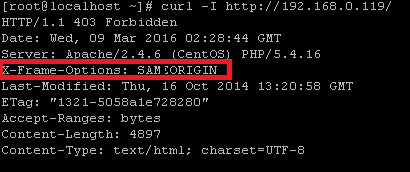
This should show the details as displayed in the following screenshot.
As you can see in the above screenshot that there is no sign of “X-Frame” parameter, which means it is disabled and your server is vulnerable. To enable X-Frame Options you need to add the following line to Apache server configuration file. Edit the apache configuration file in your favourite text editor and add the below mentioned line there.
Run following command to verify that there are no syntax errors in apache configuraiton file.
In order for changes to take effect, restart apache web server.
Now we will check again by the curl command and see its output that if the X-Frame parameter has been enabled or not.
Congratulations, our system is secure from Clickjacking attack now.
Fixing SlowLoris
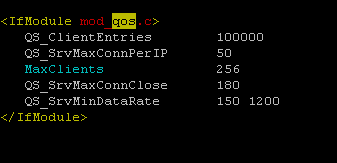
Next step is to prevent our server from SlowLoris DOS attack. There are several parameters to prevent your server from SlowLoris attack but we will use the important one; QOS module in Apache. Edit apache configuration file and add the QOS module configuration as shown in the following screenshot.
Let’s explain these parameters one by one.
- QS_ClientEntries tells us that this server will handle up to 100000 connections.
- QS_SrcMaxConnPerIP tells that 50 connections per IP will be allowed so that if the attacks is being initiated from an IP all the connection requests above 50 will be blocked (you can adjust this value to your needs).
- MaxClients is self-explanatory as total of 256 TCP connections will be made at a time.
- QS_SrvMaxConnClose setting disables KeepAlive when at least 180 connections are in use.
- QS_SrvMinDataRate settting requires a minimum of 150 bytes per second per connection, and limits the connection to 1200 bytes per second when the server reaches the MaxClients limit.
Conclusion
As already mentioned , the above listed setting should be adjusted according to your own needs and traffic statistics. But putting proper values for these parameters will ensure your web server is secure from mild to high level attack and it should perform much better and resilient to DOS attacks.