The term chroot refers to a process of creating a virtualized environment in a Unix operating system, separating it from the main operating system and directory structure. This process essentially generates a confined space, with its own root directory, to run software programs. This virtual environment runs separately from the main operating system’s root directory. Any software program run in this environment can only access files within its own directory tree. It cannot access files outside of that directory tree.
The working of Chroot Jail is that it create a directory tree where we copy or link in all the system files needed for a process to run. Then use the chroot system call to change the root directory to be at the base of this new tree and start the process running in that chroot’d environment. Since it can’t actually reference paths outside the modified root, it can’t maliciously read or write to those locations.
In this article we will setup the chroot jail environment for SSH users to encounter situations where we need some specific user access to limited resources on the system like to a web server.
1) Prerequisites:
We are using the latest CentOS 7 server with minimal packages installation. Let’s open the command line terminal and login to the root user and make sure that Open-SSH is installed and its service is running and your are connected to network.
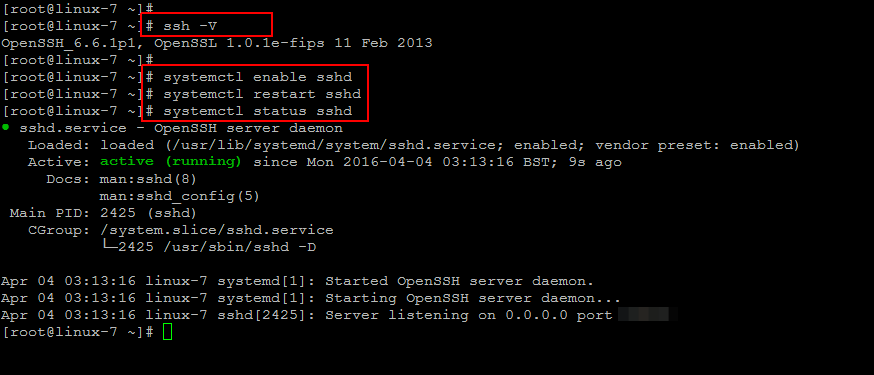
Run the command below to check the version of installed SSH package in your system.
OpenSSH_6.6.1p1, OpenSSL 1.0.1e-fips 11 Feb 2013
Then enable and start SSH services if its not already and to make sure that its enabled at boot level.
You also confirm the status of SSH and its port on which its listening by running the below command.
2) Creating Chroot Directory:
Create a new directory that will be used for chroot jail or you can also choose the existing directory to be used for chroot jail. We are going to two directories to increase the security level by using the following command.
The Jail directories can only be owned by the root so that no user can break the jail and that’s only possible if we give it the ownership or permissions to do so. You change the ownership and permissions using below commands.
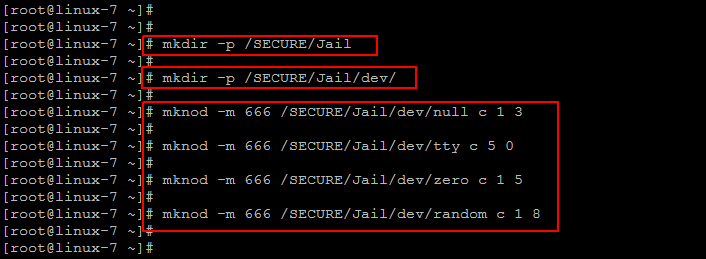
3) Creating Dev Node Entries:
There are some necessary files that we called as device nodes for ssh users access, which are required for any user process to execute in the jailed area. Let’s run the following commands to assign them or create nodes pointing to that directory useing ‘mknod’ commands shown below.
4) Bash Installation:
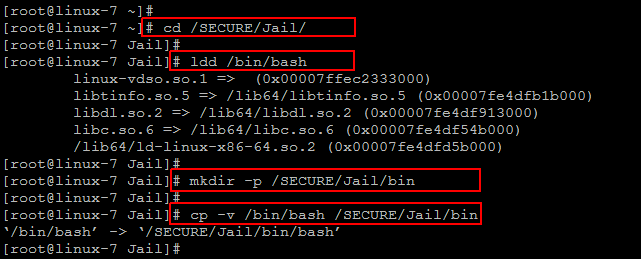
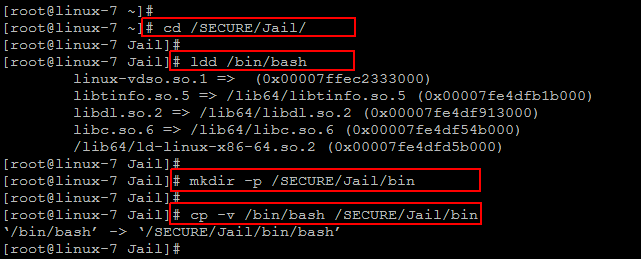
We need to install bash in the jailed directory that we have created earlier by checking the dependency of shell using below ‘ldd’ command.
Now give the following command to create and install bash in the jailed directory.
5) SSH Users Setup to CHroot
Run the following command to simply move the users information of your already created users into the chroot directory.
Then open SSH configuration file and restart its services after adding the following lines in it.
ChrootDirectory /SECURE/Jail
ForceCommand internal-sftp
In the above configurations you need to mention the user or the group that you want chroot. Saving the configurations file and restart ssh services.
Now you can connect to the allowed user_name using sftp, here you will be directed towards the chroot jailed environment.
ECDSA key fingerprint is 49:8a:9c:8f:35:e1:09:dd:rf:31:w3:a1:e1:9d:70:53.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'localhost' (ECDSA) to the list of known hosts.
Authorized uses only. All activity may be \ monitored and reported.
kash@localhost's password:
Connected to localhost.
sftp>ls
Conclusion:
Thank you for reading this article. Similarly you can expand the chroot environment according to your required access level to the particular directories and command line utilities. The chroot system call changes the root directory of the current and all child processes to the given path, and this is nearly always some restricted subdirectory below the real root of the filesystem. This new path is seen entirely as “/” by the process, and we refer to this restricted environment as the “jail”. It’s not possible to escape this jail except in very limited circumstances. Let’s enjoy and explore it in more details.