Your Gmail account can be a key for a hacker to unlock your personal details on your android smartphone. Yes, It is that simple, easy and unfortunately true!
The latest version of newly launched android market enables you to remotely install application on your smartphone. Now, this seems to be exciting! You have an android phone, a Gmail account associated to it.
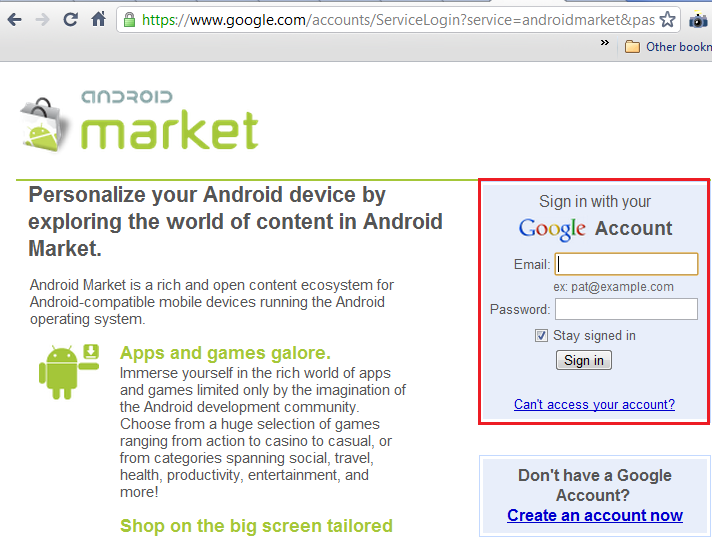
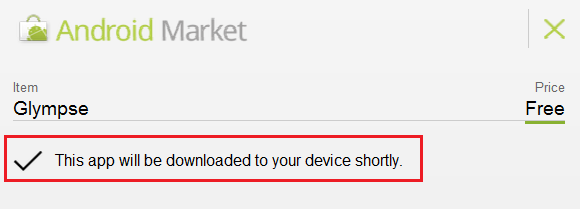
All you have to do is to open your web browser on your desktop, enter the android marker (market.android.com) and log in using your Google account. Select your favorite application and click install. The market will recognize the phone against your account and enlist the services to which the app will have access to. As soon as you agree and click “Install ”, the application will automatically start installing on your android phone (provided it is connected to the internet). You are done with remote installing the app from android market! (The entire process is illustrated)
But wait! This can be a serious security threat. Any hacker who gains unauthorized access to your Gmail account can purchase and install applications from the market to your phone remotely. As the phone does not reconfirm the installation of app and installs itself, you might not even get to know about any application remotely installed. This means that your Smartphone’s data (contacts, messages, files, documents etc.) and calls are at risk but the attacker can even find the location of victim. The German Federal Office for Information Security (BSI) is greatly concerned with the increasing attacks on mobile devices. BSI head Michael Hange states: “Just on the basis of their increasing popularity and proliferation, mobile devices are an attractive target for criminals.” With nearly countless applications in the market today, tablets, smartphones and other mobile devices have become a vulnerable target for attackers. Kaspersky has criticized this security threat owing to the new android market’s remote installation feature in its blog.
But does this hypothetical attack really make a practical sense or it is simply fictitious story? Stay tuned to the post.
To be continued