Introduction
Wickr is free, peer-to-peer encrypted messaging application for Linux, Windows, iOS, and Android. It was founded by a group of security experts in San Francisco for private communication. They define Wicker as a top secret messenger which means that nobody can track down the wickr users activities. You can send text messages, documents, audio/video, and pictures to a single or group of users. Also, you can retain the ownership of your own messages or media you share with your group. It allows you to set the expiration time to your messages, so the messages will be completely wiped out after a particular period of time. Wickr team assures that no conversions can be tracked or monitored by anyone, even by the Wickr team themselves.
Wickr uses peer-to-peer encryption method to send and receive messages. The messages from the sender doesn’t rely on any central Wickr data centers or on any third party servers. The messages are fully encrypted with AES256 method, and automatically decrypted at the receiver side. The Wickr team doesn’t know what messages are being sent and received, so you don’t have to worry about your privacy. The messages can only be read by you and the recipients on the devices you authorize. Wickr app has a privacy management feature that can be used to either block certain users that you do not want to communicate with or allow you to input which users you want to communicate with.
Wickr doesn’t need or force you to give your mobile number or mail id or any kind of personal information. However, your Internet service provider may find that you’re communicating to an anonymous person. But, they certainly could not find whom you’re talking to, or what you’re talking about.
The Wickr assures the following to the users:
- We do not upload your contact book to our servers;
- We do not know anything about you or what you do with Wickr;
- We do not sell your personal information;
- We do not store your IP address or UDID;
- We do not own the messages and media you send via Wickr;
- We do not have a back door.
Installation
Go to the Wickr downloads page, and get the latest version depending upon your device. Wickr is available for Linux, Windows, Android, and iOS.
As I use Ubuntu 64bit, I downloaded and installed the 64bit package.
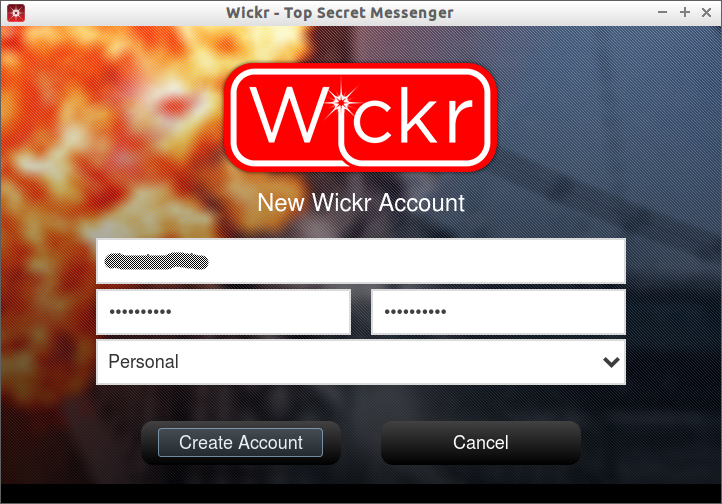
Launch it either from Menu or Dash. If you don’t have an existing account, click on the Create New Account button.
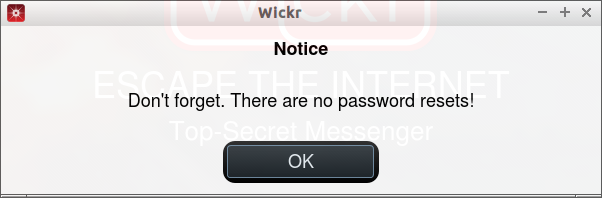
At present, Wickr doesn’t have an option to reset your forgotten password. So It is very important to note down or memorize your password.
Enter your username, password, and select the type of your account (ex.Personal), and click Create Account button.
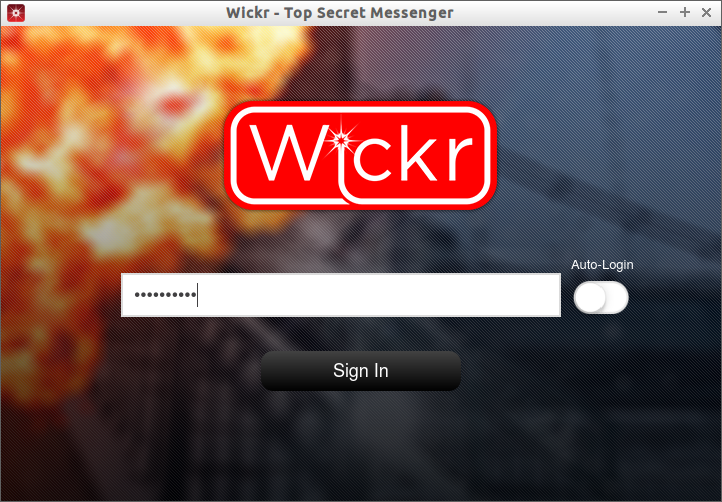
Now, login to your Wickr account.
You’ll be redirected to your Wickr dashboard. From here, you can add contacts, creating new messages and so on.
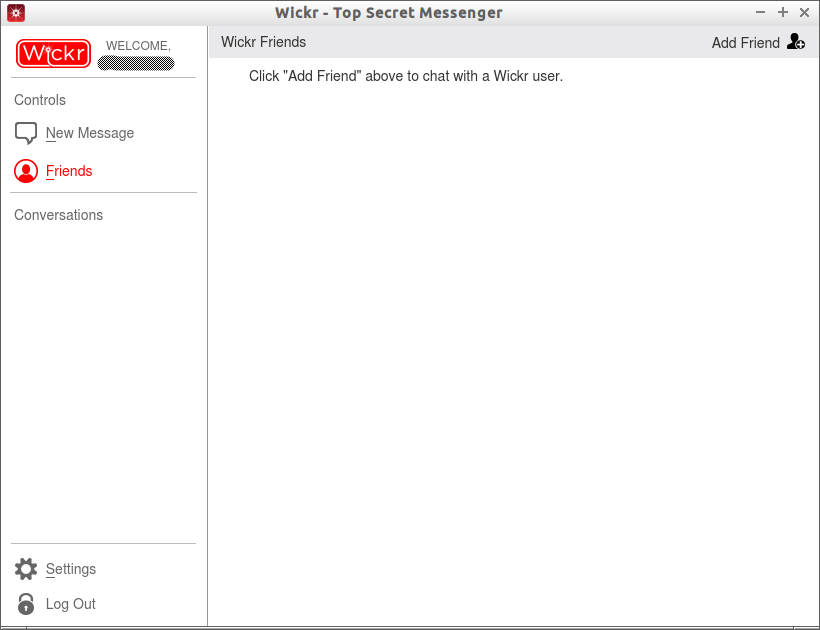
Add Friends
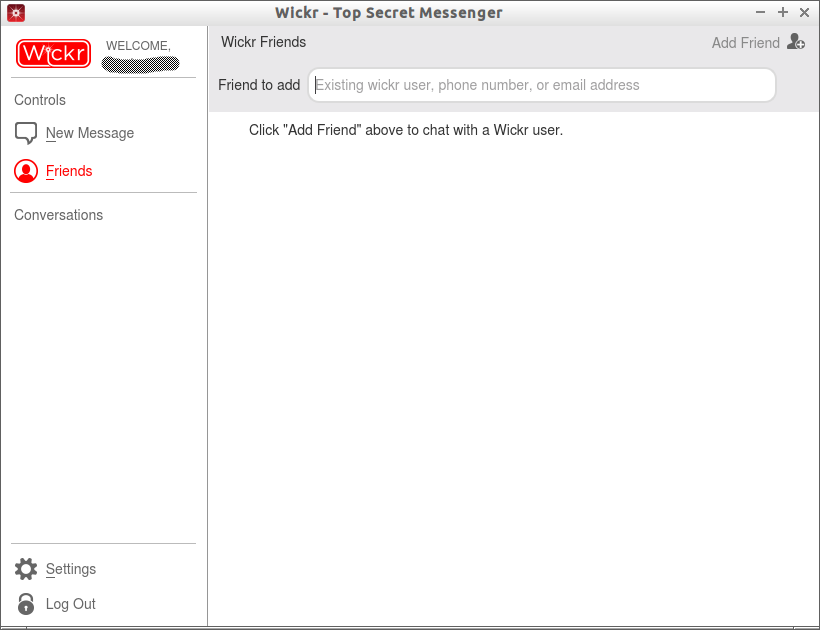
Click on the Friends button on the left. Click Add friend to add your contacts.
Enter your friends Email address, phone number or his/her Wickr ID.
Please note that your friend should register his mobile or mail id in his Wickr account. Then only you can find him with his phne number or mail id.
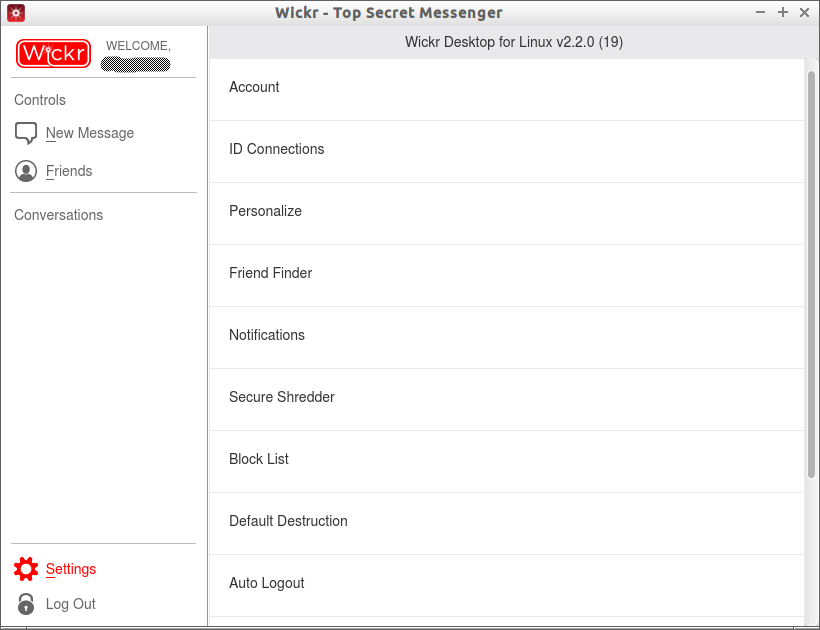
Wickr Settings
Wickr Settings can be found in the bottom left corner of the dashboard. Click on the Settings button to start customize your account.
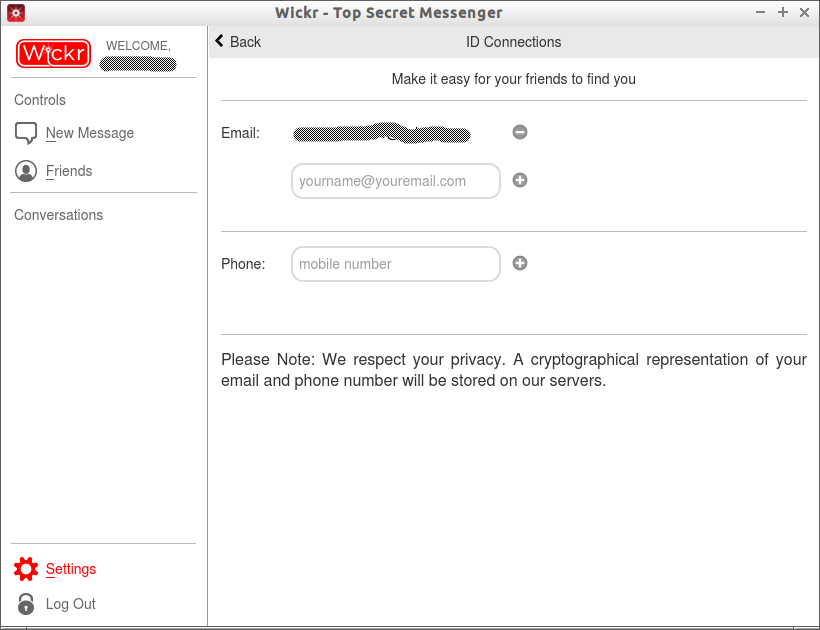
Here you can add your photo, phone number, mail id etc to make it easy for your friends to find you. Also, you can put the persons you want to block from annoying you in the Block list.
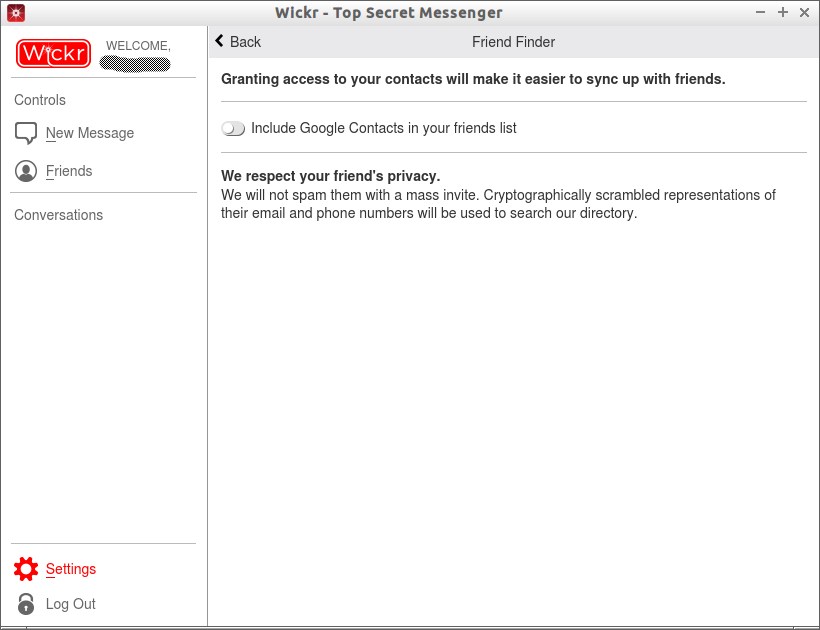
Click ID Connections to enter your Email id and phone number. Please note that Wickr have promised that it doesn’t share your details to anyone, and a cryptographical representation of your Email and phone number will be stored on Wickr servers.
A confirmation link will be sent your Email or Phone number for verification. Click on the confirmation link from Email or phone to verify your account.
That’s all. Now you can chat with your friends anonymously and securely.
Cheers!