We already knows about TACACS+ from “FreeBSD TACACS+ GNS3 and Cisco 3700 Router” article. But in your corporate company may be requirement SSN(Single Sign on) and accounting for network devices. For that you must integrate your Tacacs+ server with your corporate Domain Controller. This means in your Domain Controller have some groups for access to network device access. For users in this groups have different access level to network devices. If the user is netadmin then he will get full access and if the user is operator he will get limited access to network devices. This article will help you to do this.
Used resources:
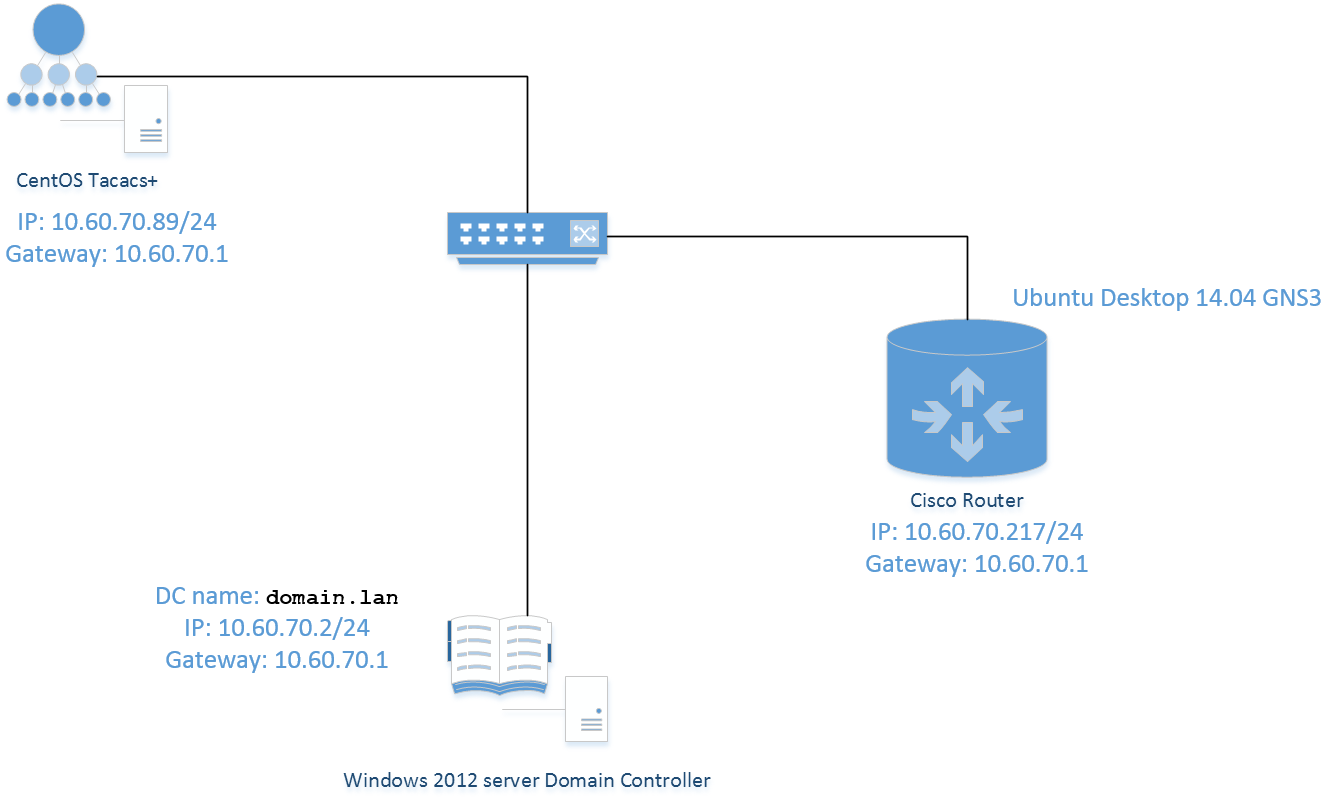
Linux Ubuntu Desktop 14.04 x64 – 10.60.70.217 GNS3 instaled and configured (Router 3600)
CentOS 6.7 x64(Tacacs+) – 10.60.70.89
Windows 2012 server – DC01-10.60.70.2, DC02-10.60.70.3
DC : domain.lan
DC user: dcuser
DC pass: DCUserPass
MSLDAP Port: 3268
DC groups: tacacsadmin, tacacsguest, tacacsmedium
Users: full, low, medium (full user is member of tacacsadmin, low user is member of tacacsguest and medium user is member of tacacsmedium groups)
Network topology will be as follows:
Update repositories and install needed packages to CentOS server:
history | grep yum | awk ‘{ $1=””; print }’ | grep -v history # commands from history
yum update
yum -y install gcc
yum -y install perl-LDAP
yum -y install bind-utils
yum -y install telnet.x86_64
yum -y install atop iotop nload iftop htop
yum -y install perl-IO-Socket-SSL
yum -y install pam-devel
yum -y install ld-linux.so.2
cat /etc/resolv.conf # Add DC IP addresses as nameserver
search domain.lan
nameserver 10.60.70.2
nameserver 10.60.70.3
Create needed folders:
history | grep mkdir | awk ‘{ $1=””; print }’ | grep -v history # commands from history
mkdir /root/tacacs
mkdir /var/log/tac_plus
mkdir /var/log/tac_plus/access
mkdir /var/log/tac_plus/acct
chmod 760 -R /var/log/tac_plus/
Download tacacs source code and compile:
cd /root/tacacs
wget http://www.pro-bono-publico.de/projects/src/DEVEL.201407301604.tar.bz2
tar jxf DEVEL.201407301604.tar.bz2 # Extract file
cd PROJECTS/ # Go to the extracted folder
./configure # configure
echo $? # Must be true as 0
make # compile
echo $? # Must be true as 0
make install # install
echo $? # Must be true as 0
Copy the configuration file, give permissions and disable firewall, Selinux.
cp /root/tacacs/PROJECTS/tac_plus/extra/tac_plus.cfg-ads /usr/local/etc/tac_plus.cfg
chmod 755 /etc/init.d/tac_plus
chmod 660 /usr/local/etc/tac_plus.cfg
chkconfig –level 0123456 iptables off
vi /etc/selinux/config # Disable SELinux
SELINUX=disabled
chkconfig –add tac_plus # Add tacacs service
chkconfig –level 2345 tac_plus on # Add tacacs daemon to startup
Note: Don’t forget that, the name of groups in tacacs configuration file isn’t written as tacacs, because tacacs automatically search in itself with this name and it searches in itself anyway with the tacacs header of groups in DC. If in configuration file will be groups as guest and admin, in DC we must create tacacsguest and tacacsadmin groups.
Configuration file will be as follows:
cat /usr/local/etc/tac_plus.cfg
#!/usr/local/sbin/tac_plus
id = spawnd {
listen = { port = 49 }
spawn = {
instances min = 1
instances max = 10
}
background = yes
}
id = tac_plus {
access log = /var/log/tac_plus/access/%Y%m%d.log
accounting log = /var/log/tac_plus/acct/%Y%m%d.log
# Configuration for connect to domain controller:
mavis module = external {
setenv LDAP_SERVER_TYPE = “microsoft”
setenv LDAP_HOSTS = “dc01:3268 dc02:3268”
setenv LDAP_BASE = “dc=domain,dc=lan”
setenv LDAP_USER = “dcuser@domain.lan”
setenv LDAP_PASSWD = “DCUserPass”
setenv REQUIRE_TACACS_GROUP_PREFIX = 1
setenv FLAG_USE_MEMBEROF = 1
exec = /usr/local/lib/mavis/mavis_tacplus_ldap.pl
}
login backend = mavis
user backend = mavis
# pap backend = mavis
host = world {
address = ::/0
prompt = “Welcome to FHN Statistika\n”
#For password generate use this “openssl passwd -1 clear_text_password” command
enable 15 = crypt $1$8hAByjzi$7tIDLo.9cHJBfW1EQN3N8.
#enable 15 = clear secret
key = “t@c@csp@$$w0rd” # Pre-shared key used between Cisco and Linux tacacs server
}
# Give access to members tacacsadmin group
group = admin {
message = “[Admin privileges]”
default service = permit
service = shell {
default command = permit
default attribute = permit
set priv-lvl = 15
}
}
# Members of tacasguest group have privilege level 1 and have enable access.
# But have not access for configure and write commands
group = guest {
message = “[Guest privileges]”
default service = permit
enable = permit
service = shell {
default command = permit
default attribute = permit
set priv-lvl = 1
cmd = configure { deny .*}
cmd = write { deny .* }
}
}
# Members of tacacsmedium group have full access but have not access for configure and enable commands:
group = medium {
message = “[Medium privileges]”
default service = permit
service = shell {
default command = permit
default attribute = permit
set priv-lvl = 15
cmd = configure { deny .*}
cmd = enable { deny .* }
}
}
}
ll /usr/local/lib/mavis/mavis_tacplus_ldap.pl # Check file path(must be so)
/usr/local/sbin/tac_plus -P /usr/local/etc/tac_plus.cfg # Check the configuration file(If everything is ok nothing will come)
service tac_plus start # Start the service
netstat -nlp | grep tac_plus # Check the listen port
tcp 0 0 :::49 :::* LISTEN 1793/tac_plus
tcpdump -nn port 49 # Sniff the port in the first console
tail -f /var/log/tac_plus/access/20140820.log # In the second console analyze the log file
tcpdump -n -e -i eth0 port 3268 # In the third console sniff the traffic going to Domain Controller
For full debugging we can use the following steps:
- Enter the command in the first console(perl-ldap module must be instaled):
env LDAP_HOSTS=”10.60.70.2″ LDAP_SERVER_TYPE=”microsoft” /usr/local/lib/mavis/mavis_tacplus_ldap.pl
- Enter the command in the second console. In the Output attribute-value-pairs must be Result – ACK:
/usr/local/bin/mavistest /usr/local/etc/tac_plus.cfg tac_plus TACPLUS full A123456789a
Input attribute-value-pairs:
TYPE TACPLUS
TIMESTAMP mavistest-2101-1408505825-0
USER full
PASSWORD A123456789a
TACTYPE AUTH
Output attribute-value-pairs:
TYPE TACPLUS
TIMESTAMP mavistest-2101-1408505825-0
USER full
RESULT ACK
PASSWORD A123456789a
SERIAL uxnEq26iaDtAp12X5kKImA=
DBPASSWORD A123456789a
TACMEMBER admin
TACTYPE AUTH
For check daemon working in debug mode you can use the following command. But I think for troubleshooting these commands is enough:
/usr/local/sbin/tac_plus -d 4088 -fp /var/run/tac_plus.pid /usr/local/etc/tac_plus.cfg
And now we are going to Linux Ubuntu Desktop machine for GNS3 installation and configuration. We will use Cisco 3600 Router in our configurations.
Open SSH and install GNS3:
apt-get update # Update the repositories, packages and kernel
apt-get dist-upgrade
apt-get install ssh # Install SSH and start
/etc/init.d/ssh start
apt-get install gns3 # Install GNS3
Create folder in some path and upload Cisco 3600 Router IOS to this folder with WinSCP(or something else). And set the Cisco 3600 Router path in our GNS3. At the end configure the GNS3 server:
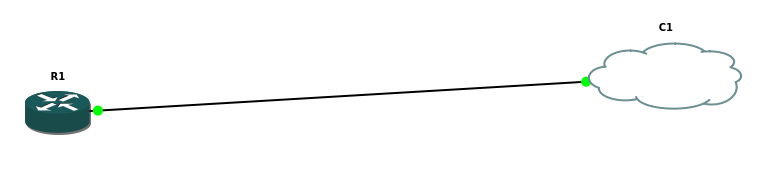
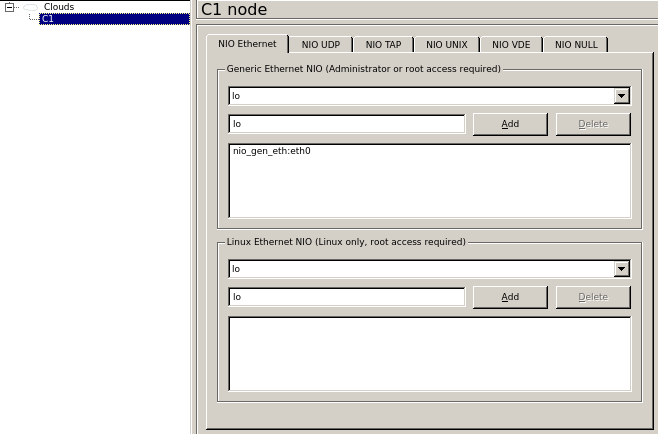
Cisco cloud configuration will be as follows:
At the end configuration for our router will be as follows:
aaa new-model
aaa group server tacacs+ TACSERVICE
server 10.60.70.89
aaa authentication login default group TACSERVICE local
aaa authentication login CONSOLE local
aaa authentication enable default group TACSERVICE enable
aaa authorization config-commands
aaa authorization exec default group TACSERVICE local
aaa authorization exec CONSOLE local
aaa authorization commands 15 default group TACSERVICE local
aaa accounting commands 15 default start-stop group TACSERVICE
ip name-server 10.60.70.2
ip name-server 10.60.70.3
interface FastEthernet0/0
ip address 10.60.70.217 255.255.255.0
no shutdown
ip default-gateway 10.60.70.1
tacacs-server host 10.60.70.89
tacacs-server timeout 2
tacacs-server key t@c@csp@$$w0rd # Pre-shared key used between Cisco and Linux tacacs server
line con 0
login authentication CONSOLE
line vty 0 15
do write memory # Save the configurations
Try to connect to our Cisco 3600(IP: 10.60.70.217) router from subnet 10.60.70.0/24:
root@squidprimary:~ # telnet 10.60.70.217
Trying 10.60.70.217…
Connected to 10.60.70.217.
Escape character is ‘^]’.
Welcome to Corp R
Username: low
Password: A123456789a
[Guest privileges]
R1>
In the /var/log/tac_plus/access/20140820.log log file we must see the following line:
2014-08-20 09:33:02 +0500 10.60.70.217: shell login for ‘low’ from 10.60.70.50 on tty226 succeeded
For debug Router we can use the following commands.
Debug for AAA:
debug aaa per-user
debug aaa authentication
debug aaa authorization
debug aaa accounting
Debug for tacacs we can use the following commands:
debug tacacs authentication
debug tacacs authorization
debug tacacs accounting
debug tacacs events
debug tacacs packet