Lately i haven’t posted much because i have been busy working on some programming projects, but today i will share a python script with you guys. This script is written in pure python and it can be used to grab banners from different services running on your subnet. Some of these services are SSH, Telnet, FTP, SMTP etc.
This script is useful to system administrators to check their services and penetration testers to check the service for different vulnerabilities. We use the socket library, which allows us to create a socket and then we send garbage data to a specific service. After sending the garbage data, we wait for a response from the service we are testing and print the results of this response on the screen.
Features Of The Script – Support For SSH – Support For FTP – Support For SMTP – Vulnerability Checking
You can add more ports to the portList list and the script will try to grab banners of services running on these ports if there is any. The program accepts command line arguments. If you want to check your banners for vulnerabilities you need text file with vulnerable banners on each line of this file. Do not forget to put the IP Address of your subnet while you run the script, if you want you can use it only for banner grabbing, or banner grabbing and vulnerability checking. Do not use any command line argument if you want to run the script only for banner grabbing.
Alternatively, you can just use a banner generator.
#!/usr/bin/python
import socket
import sys
import os
#grab the banner
def grab_banner(ip_address,port):
try:
s=socket.socket()
s.connect((ip_address,port))
banner = s.recv(1024)
print ip_address + ':' + banner
except:
return
def checkVulns(banner):
if len(sys.argv) >=2:
filename = sys.argv[1]
for line in filename.readlines():
line = line.strip('\n')
if banner in line:
print "%s is vulnerable" %banner
else:
print "%s is not vulnerable"
def main():
portList = [21,22,25,80,110]
for x in range(0,255):
for port in portList:
ip_address = '192.168.0.' + str(x)
grab_banner(ip_address,port)
if __name__ == '__main__':
main()
Usage Of The Script
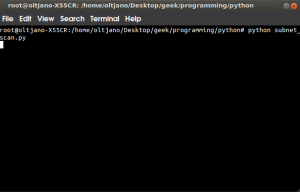
# python <script_name.py>
Screenshots: Figure 1 shows how to run this script. Before running the script make sure you put your ip address in the script. You need some basic python skills to work with this script. Everything is self explanatory.
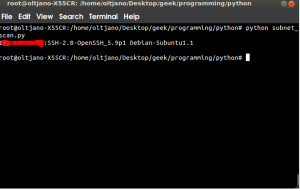
After running the script give it some time because it is scanning all machines in your subnet, so it will take some time. The script does everything for you, just wait until it finishes the job and get the output like shown in Figure 2.