WireShark 2.2.2: 30 bug fixes
WireShark is the most popular network protocol analyzer. Admins use it mostly for troubleshooting, developers for testing new protocols, and it's also a very...
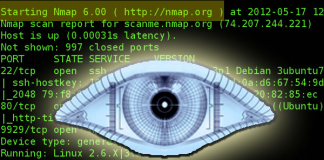
10 Practical Examples Of Linux ‘nmap’ Command
About Nmap
Nmap is a tool used for determining the hosts that are running and what services the hosts are running. Nmap can be a...
Google Chrome 29 Has Been Released, 25 New Security Fixes
Hello Google Chrome Users! This article is a short update for all of you guys that use Google Chrome as your web browser or...
Protect Yourselves From Attacks On Public WiFi Networks With WiFi Protector
All the anti-virus programs in the world won’t help you if you log on the public WiFi at a coffee shop. Most of us...
Enhancing Linux Security with Network Access Control Software: Safeguarding Your Networks...
In an era where cyber threats continue to evolve, ensuring the security of computer networks and sensitive data is paramount. As a widely used...
Data Security and Privacy in Cloud Migration
Cloud-based computing has revolutionized the way businesses operate. It provides secure data storage as well as cost-efficient access to vast amounts of information. There...
Risks to Consider When Using Linux
Linux is a free and open-source operating system that's popular among developers, businesses, and individuals. The flexibility and customizability of Linux make it an...
Sandboxed Gentoo
Introduction
This article is a guide on installing Gentoo in another Linux distribution (Arch, in this case). Look at it like a BSD Jail. It's...
How To Install Linux Kernel 3.12.4 In Ubuntu
Linux Kernel 3.12.4 has been officially released with fixes for inet6_init() cleanup order, seqlock deadlock in ip6_finish_output2 and Report Descriptor for Logitech MOMO Force. In this...
PeerGuardian: A Privacy Oriented Firewall
PeerGuardian is a privacy oriented firewall application. It blocks connections to and from hosts specified in huge blocklists (thousands or millions of IP ranges)....
Remove The Password Of A Password Protected PDF Files
This brief tutorial describes how to remove the password protection from the PDF files. Please note that we are not going to hack or...
Knockd – Detailed And Simpler
As I could see there are lot of articles about knockd and it’s implementation. So, what are my efforts to make this unique? I...
How To Install And Use Untangle Firewall
Introduction
Untangle is very lightweight, easy to install and easy to use but very effective firewall operating system. It makes you enable to protect, monitor and...
ChatCrypt: Let us Chat Secure
Just like most of you, I also really hate to be monitored by third parties when i am communicating with Friends/Colleagues on Internet. Now...
Enhancing Security Measures: Best Practices for Linux Servers in WordPress Environments
In the ever-evolving landscape of web development, the synergy between Linux servers and WordPress has become a cornerstone for startups looking to establish a...
How To Configure Vsftpd With SSL/TLS On CentOS 7
A few weeks before, We have shown you how to install and configure a basic FTP server on CentOS 7. Today, In this brief...
IPFire – An Open Source, And Free Firewall Distribution
IPFire is an open-source Linux distribution with many useful features such as web based GUI, web proxy, intrusion detection, VPN, virus scanner, and many....
Why Do I Need a Firewall?
Unix/Linux is well known for its security and nobody doubts that. But why not work to make your machine even more secure. Securing your...