Tripwire is an open-source security and data integrity tool useful for monitoring and alerting on specific file change(s) on a range of systems. If any file gets modified or changed, it will send a alert to you. If the changes are valid, the you can accept the changes by updating the tripwire database.
Install Tripwire
On Ubuntu/Debian:
sk@sk:~$ sudo apt-get install tripwire
Select Internet site and Enter.
Enter the mail (FQDN) name.
Now the Tripwire configuration task starts.
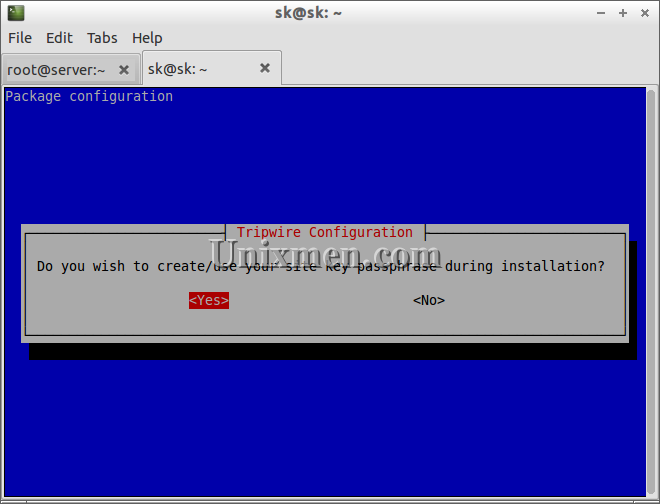
Select Yes to create site key pass phrases.
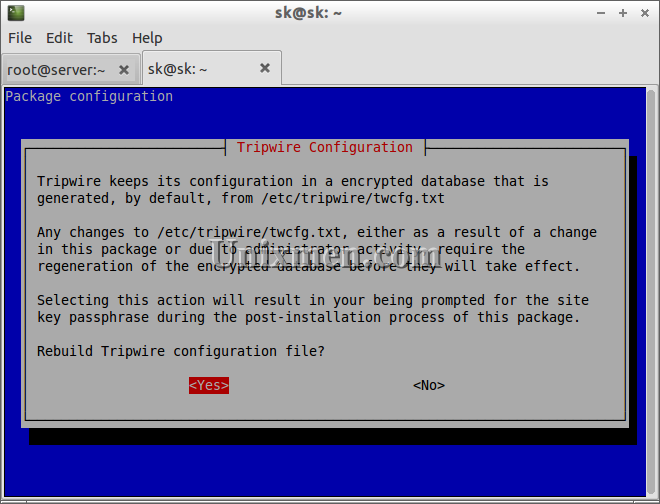
Select yes to rebuild the Tripwire configuration file.
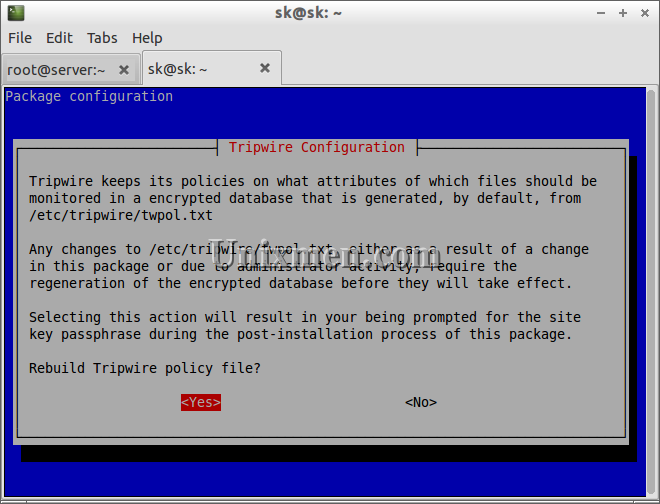
Rebuild Tripwire policy file. Select Yes.
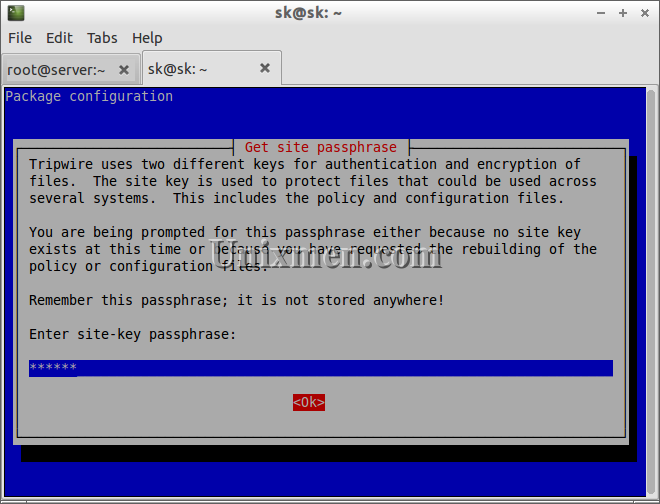
Enter site-key passphrase.
Re-enter site-key passphrase.
Enter local key passphrase.
Re-enter passphrase.
Now the Tripwire has been installed with local and site key passphrases.
On CentOS/RHEL, Tripwire will not be found on official repository. So add EPEL repository to install Tripwire:
[root@server ~]# rpm -ivh http://dl.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
Now install Tripwire:
[root@server ~]# yum install tripwire -y
Create keyfile pass phrases
Likewise in Ubuntu local and site keyfile passphrases will not be created when installing Tripwire. Enter the following commands to create site and local keyfile pass phrases for Tripwire:
[root@server ~]# tripwire-setup-keyfiles ---------------------------------------------- The Tripwire site and local passphrases are used to sign a variety of files, such as the configuration, policy, and database files. Passphrases should be at least 8 characters in length and contain both letters and numbers. See the Tripwire manual for more information. ---------------------------------------------- Creating key files... (When selecting a passphrase, keep in mind that good passphrases typically have upper and lower case letters, digits and punctuation marks, and are at least 8 characters in length.) Enter the site keyfile passphrase: Verify the site keyfile passphrase: Generating key (this may take several minutes)...Key generation complete. (When selecting a passphrase, keep in mind that good passphrases typically have upper and lower case letters, digits and punctuation marks, and are at least 8 characters in length.) Enter the local keyfile passphrase: Verify the local keyfile passphrase: Generating key (this may take several minutes)...Key generation complete. ---------------------------------------------- Signing configuration file... Please enter your site passphrase: Wrote configuration file: /etc/tripwire/tw.cfg A clear-text version of the Tripwire configuration file: /etc/tripwire/twcfg.txt has been preserved for your inspection. It is recommended that you move this file to a secure location and/or encrypt it in place (using a tool such as GPG, for example) after you have examined it. ---------------------------------------------- Signing policy file... Please enter your site passphrase: Wrote policy file: /etc/tripwire/tw.pol A clear-text version of the Tripwire policy file: /etc/tripwire/twpol.txt has been preserved for your inspection. This implements a minimal policy, intended only to test essential Tripwire functionality. You should edit the policy file to describe your system, and then use twadmin to generate a new signed copy of the Tripwire policy. Once you have a satisfactory Tripwire policy file, you should move the clear-text version to a secure location and/or encrypt it in place (using a tool such as GPG, for example). Now run "tripwire --init" to enter Database Initialization Mode. This reads the policy file, generates a database based on its contents, and then cryptographically signs the resulting database. Options can be entered on the command line to specify which policy, configuration, and key files are used to create the database. The filename for the database can be specified as well. If no options are specified, the default values from the current configuration file are used.
Initialize Tripwire Database
On Ubuntu/Debian:
sk@sk:~$ sudo tripwire --init Please enter your local passphrase: Parsing policy file: /etc/tripwire/tw.pol Generating the database... *** Processing Unix File System *** ### Warning: File system error. ### Filename: /var/lib/tripwire/sk.twd ### No such file or directory ### Continuing... ### Warning: File system error. ### Filename: /etc/rc.boot ### No such file or directory [...] ### Continuing... The object: "/proc/sys/fs/binfmt_misc" is on a different file system...ignoring. Wrote database file: /var/lib/tripwire/sk.twd The database was successfully generated.
On CentOS/RHEL:
[root@server ~]# tripwire --init Please enter your local passphrase: Parsing policy file: /etc/tripwire/tw.pol Generating the database... *** Processing Unix File System *** ### Warning: File system error. ### Filename: /dev/kmem ### No such file or directory ### Continuing... [...] ### Continuing... Wrote database file: /var/lib/tripwire/server.unixmen.com.twd The database was successfully generated.
In the both above outputs, you may notice that a error called “No such file or Directory” and “file system error”. This is because the tripwire scans every files/directories which are mentioned in the tripwire configuration file. The files/directories might not be existed in your system. Comment the lines which are showing this error in the tripwire config file or leave it as is.
To do that open the file /etc/tripwire/twpol.txt and comment the file/directory lines which are not present in your system.
On Ubuntu/Debian:
sk@sk:~$ sudo vi /etc/tripwire/twpol.txt
On CentOS/RHEL:
[root@server ~]# vi /etc/tripwire/twpol.txt
Find and comment the lines which are showing error. Save and close the file.
Testing Tripwire
Let us add a file called unixmen to see how Tripwire IDS works.
[root@server ~]# touch unixmen
Now run the Tripwire interactive command.
[root@server ~]# tripwire --check --interactive
Once you run this command, tripwire will collect all the files/directories changes/modifications and automatically open the result in the vi editor.
This is how your output looks:
Open Source Tripwire(R) 2.4.1 Integrity Check Report Report generated by: root Report created on: Friday 21 June 2013 02:05:02 PM IST Database last updated on: Never =============================================================================== Report Summary: =============================================================================== Host name: server.unixmen.com Host IP address: Unknown IP Host ID: None Policy file used: /etc/tripwire/tw.pol Configuration file used: /etc/tripwire/tw.cfg Database file used: /var/lib/tripwire/server.unixmen.com.twd Command line used: tripwire --check --interactive =============================================================================== Rule Summary: [...]
Scroll down through the file and it will show a notification that a new file called unixmen have been added:
[...] Remove the "x" from the adjacent box to prevent updating the database with the new values for this object. Added: [x] "/root/unixmen" Modified: [x] "/root" [...] ------------------------------------------------------------------------------- *** End of report *** Open Source Tripwire 2.4 Portions copyright 2000 Tripwire, Inc. Tripwire is a registered trademark of Tripwire, Inc. This software comes with ABSOLUTELY NO WARRANTY; for details use --version. This is free software which may be redistributed or modified only under certain conditions; see COPYING for details. All rights reserved.
If this is a valid, you can accept the changes by updating the Tripwire database. Or just remove the x mark and update database. Type :q to save and exit from the file. It will ask the local passphrase, enter the passphrase. Now the tripwire database has been updated.
View Tripwire report files
Normally Tripwire report file is stored under /var/lib/tripwire/report/ directory with extension .twr. You can’t view this type of files using any editor. First you have to convert the files to txt file. To do that enter the following command in the terminal:
[root@server ~]# twprint --print-report --twrfile /var/lib/tripwire/report/server.unixmen.com-20130621-141518.twr > /tmp/tripwire_report.txt
Now open it using your favorite editor:
[root@server ~]# vi /tmp/tripwire_report.txt Note: Report is not encrypted. Open Source Tripwire(R) 2.4.1 Integrity Check Report Report generated by: root Report created on: Friday 21 June 2013 02:15:18 PM IST Database last updated on: Never ============================================================================== Report Summary: ================================================================ ============== Host name: server.unixmen.com Host IP address: Unknown IP Host ID: None Policy file used: /etc/tripwire/tw.pol Configuration file used: /etc/tripwire/tw.cfg Database file used: /var/lib/tripwire/server.unixmen.com.twd Command line used: tripwire --check --interactive =============================================================================== Rule Summary: ====================================== [...]
To view the Tripwire configuration location:
[root@server ~]# twadmin --print-cfgfile ROOT =/usr/sbin POLFILE =/etc/tripwire/tw.pol DBFILE =/var/lib/tripwire/$(HOSTNAME).twd REPORTFILE =/var/lib/tripwire/report/$(HOSTNAME)-$(DATE).twr SITEKEYFILE =/etc/tripwire/site.key LOCALKEYFILE =/etc/tripwire/$(HOSTNAME)-local.key EDITOR =/bin/vi LATEPROMPTING =false LOOSEDIRECTORYCHECKING =false MAILNOVIOLATIONS =true EMAILREPORTLEVEL =3 REPORTLEVEL =3 MAILMETHOD =SENDMAIL SYSLOGREPORTING =false MAILPROGRAM =/usr/sbin/sendmail -oi -t
To view the Policy file location:
[root@server ~]# twadmin --print-polfile
Schedule Tripwire check Using Cron
Open the /etc/crontab file and append the lines as shown below:
[root@server ~]# vi /etc/crontab 00 12 * * * /usr/sbin/tripwire --check
The above command will execute Tripwire check daily at 12’o clock.