Introduction to SSH
Introduction
What is SSH? Why use SSH?
SSH is a network protocol similar to telnet or FTP, yet slightly different because it offers secure data communication....
How To Manage Multiple SSH Sessions Using Cluster SSH And PAC...
About SSH
We, all, know what is SSH, right? SSH, stands for Secure Shell (sometimes known as Secure Socket Shell), is a Cryptographic Protocol that...
Why Do I Need a Firewall?
Unix/Linux is well known for its security and nobody doubts that. But why not work to make your machine even more secure. Securing your...
How To Monitor The Performance With Cisco IPSLA
In the early 70’s the computer networks appeared for the first time. These networks were rapidly converted into an absolute necessity for all the...
Linux Trojan Stealing Bank Data From Linux Users
We love linux and one of the reason why we love it is the high security it offers. Shopping in a linux box is...
ChatCrypt: Let us Chat Secure
Just like most of you, I also really hate to be monitored by third parties when i am communicating with Friends/Colleagues on Internet. Now...
News from Kaspersky Lab: Tor is protecting criminals
In a previous article I wrote a bit about Tor. Free browser, relays bouncing your IP all over the world. Guaranteed anonymity. This is...
How to Leverage Cybersecurity With Linux Systems
Linux is one of the operating systems such as Windows, Mac OS, and IOS. Linux also powers the Android system that most popular platforms...
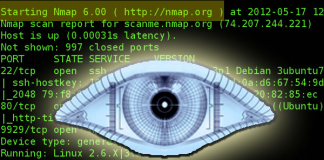
10 Practical Examples Of Linux ‘nmap’ Command
About Nmap
Nmap is a tool used for determining the hosts that are running and what services the hosts are running. Nmap can be a...
6 Factors that Make Linux Important for your Small Business
A huge number of modern companies know about Linux firsthand. Many of them have been using various distributions in one form or another for...
5 Linux Cybersecurity Mistakes Small Businesses Commonly Make
Running a small business on Linux doesn’t mean having a small workload. You need to take care of so many things yourself or with...
5 Tips for an Effective Cyber Security Strategy for Your Business
Cyber attacks have drastically advanced, with criminals using more sophisticated tools to steal and misuse company data. This has increased ransomware, phishing attempts, DoS...
Arachni the Security scanning tool for Web
Introduction:
Arachni is a fully featured web security scanning tool, it is based on ruby framework.It is an open source, modular and high performance tool....
Tips to Enhance Linux Security
In recent years, the usage of linux operating systems has increased a bit. Though, not at that impressive rate, there have been more users...
Enhancing Security Measures: Best Practices for Linux Servers in WordPress Environments
In the ever-evolving landscape of web development, the synergy between Linux servers and WordPress has become a cornerstone for startups looking to establish a...
5 Cybersecurity Tips to Help Linux Users Protect Their Computers
Cybercrime is a growing threat that has caused most internet users to rethink how they protect their data and information. Cybercriminals are getting more...
Knockd – Detailed And Simpler
As I could see there are lot of articles about knockd and it’s implementation. So, what are my efforts to make this unique? I...
How to Configure Sshguard With IPFW Firewall On FreeBsd ?
There is an old saying that the only safe computer is one that’s disconnected from the network, turned off, and locked in an underground...